New Claims Report finds attackers utilizing more sophisticated, dangerous tactics and techniques

The events of the last year radically shifted the nature of work. The rush to adapt to remote work combined with an increased reliance on technology fueled another change — cybercriminals capitalized on the shift in the cyber landscape to exploit technologies, target new industries, and make existing attack techniques more successful. Now more than ever, organizations large and small face the crucial task of addressing cyber risk. Our H1 2021 Cyber Insurance Claims Report analyzed claims data through June 2021 from customers in the United States and Canada and found that attackers utilized a variety of attack techniques to compromise a wide range of organizations.
Our visibility into cyber incidents comes from three primary sources: our policyholders reporting incidents and claims, data the National Association of Insurance Commissioners (NAIC) shares with us, and finally, from the tens of thousands of insurance applications we receive each year. This is our second year compiling data to assess trends in cyber insurance.
Understanding the tactics and techniques that threat actors employ to gain access to an organization is essential to creating an effective cybersecurity program. Three new trends: insecure remote access, supply chain attacks, and an increased risk for small and midsize businesses have the potential to be especially devastating for organizations if they are not addressed and mitigated.
Insecure remote access leads to attacks
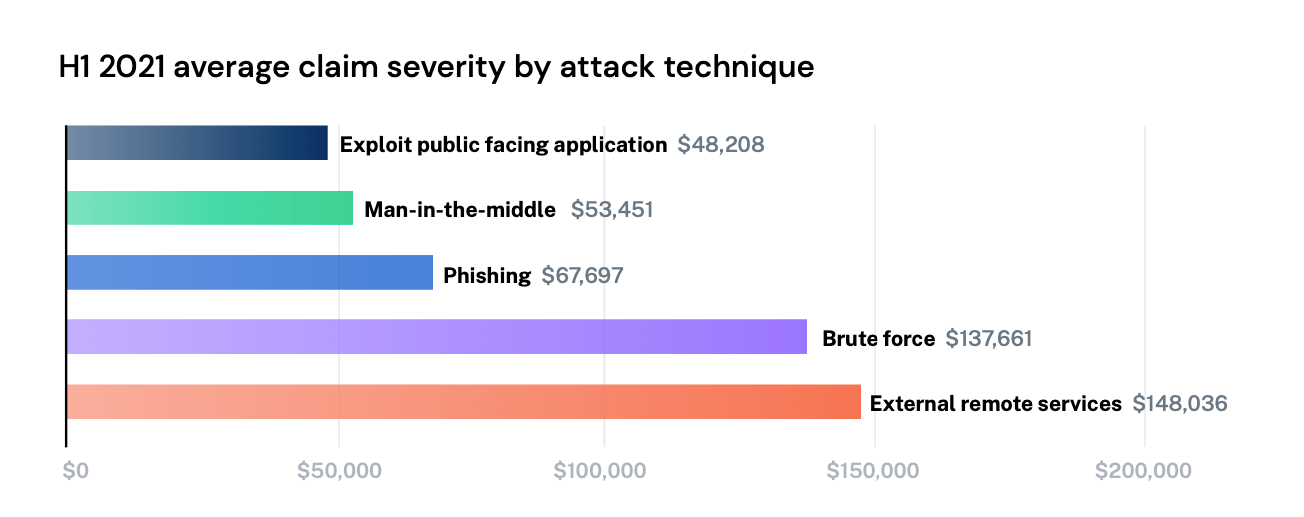
Remote desktop protocol (RDP) is a popular remote access solution often used in Windows environments — and a popular attack vector for threat actors. RDP enables users to access their well-known Windows desktop from anywhere, but it is vulnerable to various attacks. For example, attackers can intercept RDP connections or get a remote computer to execute unauthorized programs. Additionally, the computer running RDP is inside your organization’s network; this gives attackers internal access, potentially allowing them to pivot to other, more devastating cyber attacks such as ransomware.
The rate of policyholders who experienced a claim due to exposed RDP also increased from 29% to 40%, and the severity of these incidents increased by 103%.
Due to the pandemic, we saw a sharp uptick in RDP usage. The number of organizations with RDP enabled when they applied for insurance nearly doubled from the first half of 2020 to 2021. As a result of the inherent risk associated with RDP, Coalition scans for it, and we won’t insure organizations until they disable it.
The risk you can’t control: supply chain attacks
Digital supply chains provide critical resources for many organizations. Unfortunately, attacks against a digital vendor can impact several organizations in the same supply chain, allowing attackers to easily and effectively impact many organizations at once. Supply chain risk is difficult to mitigate as nearly all businesses require internet access, and digital transformations lead to increased reliance on cloud services and their vendor partners. This leads organizations to undertake risks they can’t control and expose their critical information to an environment they do not own.
We saw the devastating potential of supply chain attacks with Mimecast, SolarWinds, and Microsoft Exchange. Over 1,000 Coalition policyholders were exposed to the Microsoft Exchange vulnerability, which our in-house incident response team worked quickly to remediate. However, the Exchange vulnerability continues to pose a risk as attackers continue to discover new tactics to exploit this vulnerability despite a series of security patches.
We saw the devastating potential of supply chain attacks with Mimecast, SolarWinds, and Microsoft Exchange. Over 1,000 Coalition policyholders were exposed to the Microsoft Exchange vulnerability, which our in-house incident response team worked quickly to remediate. However, the Exchange vulnerability continues to pose a risk as attackers continue to discover new tactics to exploit this vulnerability despite a series of security patches.
Our Claims report found a 51% increase in business email compromise claims, 28% increase in funds transfer fraud claims, and more widespread supply chain attacks in 2021.
Smaller organizations became a target
Cybercriminals are opportunistic, particular about selecting their targets. We have found that an organization's technological choices are far more indicative of their risk than their industry — anyone could become the target of a cyber attack. Still, it is becoming more profitable for criminals to target small and midsize businesses.
Download the full H1 2021 Cyber Insurance Claims report here to learn more about these trends and our predictions for the remainder of 2021.
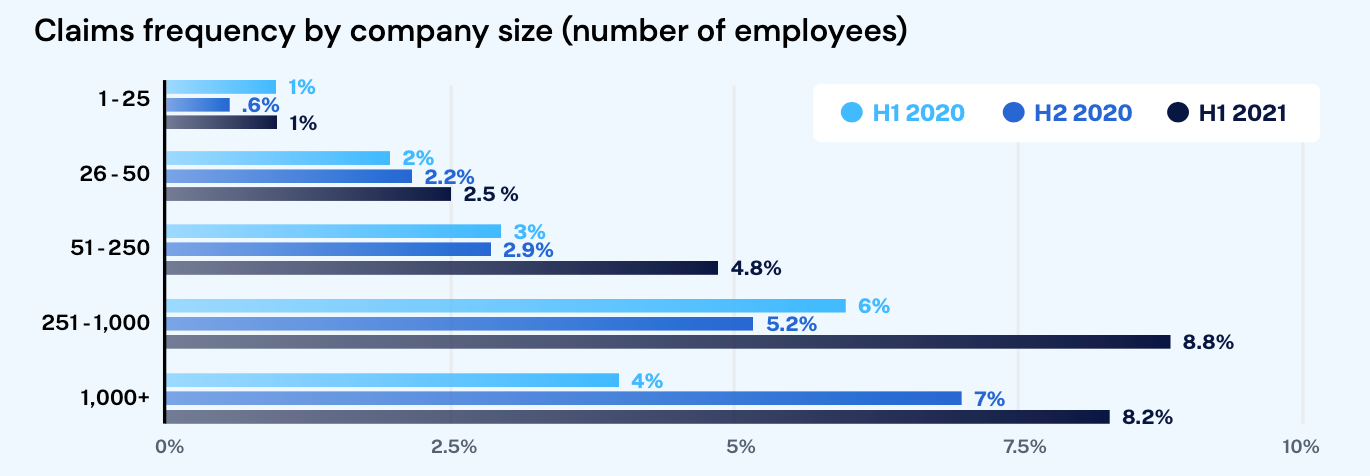
Small and midsize businesses historically experienced fewer claims, but we've seen an increase in claims frequency by 57% for organizations with 250 employees or less. Cybercriminals can extort growing amounts from organizations following a ransomware or funds transfer fraud attack. Additionally, while new trends in cybercrime continue to make headlines, tried and true tactics like business email compromise (BEC) remain a threat. BEC incidents continue to be the most widespread attack as email is the dominant attack surface of most organizations large and small. BEC events can also precipitate more devastating attacks once an attacker has gained access to a network.
Security partner spotlight: Secure your network with Twingate
The evolution of the cyber landscape over the last year has shown that cyber risk impacts everyone. To enable organizations to control their risk profile in a highly connected environment, Coalition partners with leading cybersecurity solutions providers to offer everything from training to tools to identity and access management, and endpoint protection. One such partner, Twingate, offers a zero trust network access (ZTNA) solution to replace legacy VPNs and help secure your network access points, making hybrid work models safer, more secure, and highly scalable.
“Every single network request is now its own perimeter with its own rules.” - Alex Marshall, Chief Product Officer, Twingate (a Coalition security partner)
During Coalition Security Week 2021, Chief Product Officer and Co-founder of Twingate, Alex Marshall, joined us in a fireside chat to discuss the evolution of an organization’s digital perimeter and how Twingate can help keep critical infrastructure secure.
Linked Entry ID: 5blTkg50TRbnZ9rXWDwbuL
Address your risk holistically with Coalition Control
Mitigating cyber risk is more complex than addressing a single attack vector. To monetize cybercrime, criminals utilize a wide array of attack techniques to access an organization’s networks and critical systems. Coalition Control, our free risk monitoring platform, enables organizations to make good decisions to address and mitigate their cyber risk, reducing their exposure to would-be attackers. Also inside the Coalition Control ecosystem is information about all of our cybersecurity solutions partners.