Fortinet zero-day vulnerability: What your clients need to know
New cyber risks and vulnerabilities pop up daily as threat actors adapt their methods to successfully carry out cyber crimes. Brokers have a unique challenge in communicating these evolving threats to their clients. We’re here to help you understand the latest vulnerabilities so you can communicate them to your clients before a vulnerability becomes a claim.
On October 10, 2022, Fortinet announced that its researchers discovered a new vulnerability within three of the company’s products:
FortiOS
FortiProxy
FortiSwitchManager
This zero-day vulnerability (CVE-2022-40684) should spell concern for organizations that employ Fortinet devices because it allows attackers to gain administrative access to software without requiring them to log in.
Fortinet has reported cases of active exploitation of this vulnerability, and Coalition has also seen evidence of attack on our global reconnaissance network. Since October 13, Coalition has observed 96 unique IP addresses trying to exploit this vulnerability.
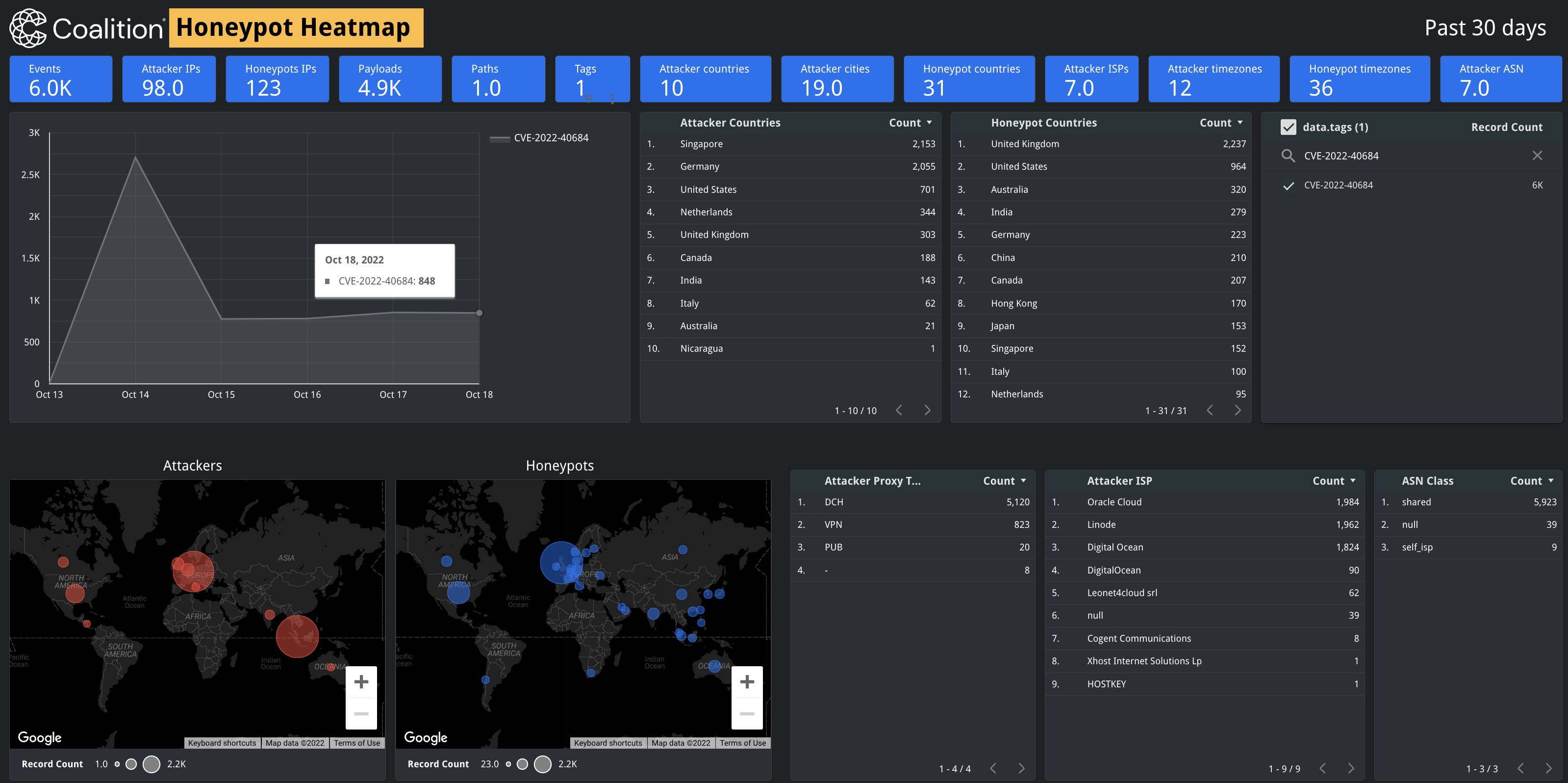
Fortinet data from Coalition's global honeypot network
At this time, Coalition has observed over 625,000 Fortinet devices exposed directly to the internet. All of this evidence underscores the importance of taking the necessary remediation steps. If you haven’t already, Coalition recommends urgently notifying your clients to do so as soon as possible.
What policyholders need to know
Here’s what you should share with your clients. Currently, there are several ways you can reduce your exposure to this vulnerability or remediate it entirely. The absolute best solution is to remove the affected components from the internet.
Fortinet has also published remediation steps in an advisory. We recommend referring to this advisory to remediate the vulnerability if you are unable to remove the affected components from the internet.
Steps to reduce risk
Remove the administration endpoints from the internet. This has the additional benefit of not being accessible if further vulnerabilities are found in this product.
Follow Fortinet’s advisory to reduce exposure to this vulnerability.
Update your Fortinet software to the latest version to patch the vulnerability.
Sign in to Coalition Control to get a live assessment of your digital risk for this vulnerability (and any others).
If you think you have been compromised, immediately contact Coalition for help.
How Coalition is responding
Once the vulnerability was disclosed, our teams at Coalition sprang into action. Over the past week, we have monitored policyholder assets and observed attacker activity for this specific vulnerability.
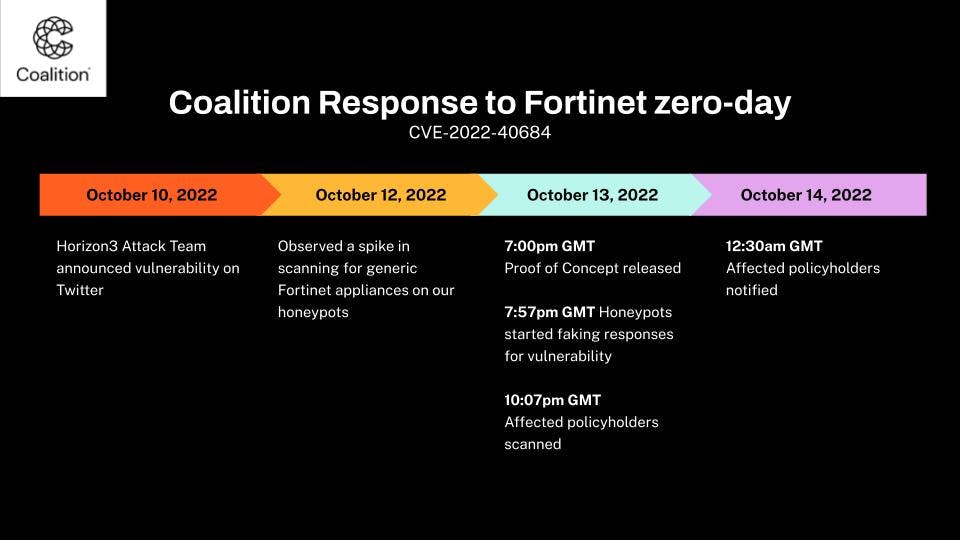
One of the first things we did was modify our scanning engine. This allowed us to determine which of our policyholders were exposed to the vulnerability and quickly notify them of any actions they may need to take. Through our network of honeypots worldwide, we can see what vulnerabilities attackers are on the hunt for and how they are attempting to exploit these vulnerabilities.
The first observations of attacker activity for this Fortinet vulnerability occurred on October 13, 2022. The information we have gathered since then has helped us assess the risk posed to our policyholders and monitor any further developments in attacker exploitation.
Coalition will continue to monitor the situation, rescanning our policyholders and alerting them to any new, impacted asset we may discover.
Help your clients take Control
One of the best ways to help your clients stay safe is to urge them to use Coalition Control. Not only will it help them assess their exposure to this Fortinet vulnerability but also all future vulnerabilities. Pair this with educating them on cybersecurity best practices and the importance of keeping their software up to date, and you have a recipe for success.







