November Risk Roundup: CISA steps up to compete for valuable cyber defender talent

Money makes the world go-'round, as the saying goes, and that applies to the world of cybersecurity. Both attackers and defenders can be motivated by financial gain — if there is money to be made, it is a strong incentive. Unfortunately, criminals will find ways to steal money that doesn’t belong to them if the reward is high enough, and it’s evident that paying competitive salaries is a great way to ensure you attract and retain talented cybersecurity practitioners. The tricky part is finding the right balance between paying security salaries vs. losing money to cyber criminals.
1. CISA announces new hiring system for cyber talent
Although the cyber skills shortage is likely overblown, there’s no doubt that hiring and retaining cybersecurity professionals is challenging. Competitive salaries and career development opportunities like the DHS CTMS are a great first step to helping the US Government compete. I can attest from personal experience that disruptions like government shutdowns, challenging work environments with politically-motivated strategy changes, and restrictive requirements for clearances are reasons to avoid or even leave government service. Tech companies are willing to overlook minor issues like speeding tickets or not wearing a suit every day, and they pay very well.
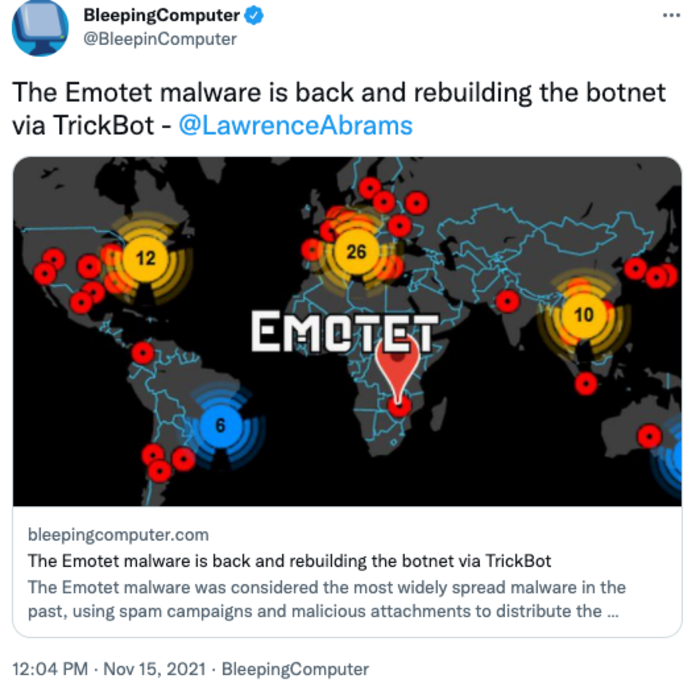
2. Emotet malware makes a comeback
The forces at play in cybercrime follow a very predictable and well-known pattern: supply and demand. Cybercrime tools are now a commodity, so it’s not unexpected to see a major takedown, like Emotet, being circumvented since criminals need infrastructure and are willing to pay. When a cybercrime gang is taken down, organizations should use the downtime to shore up cyber defenses because attackers will always be back, even with strict enforcement.
3. FBI infrastructure hacked
The word “hack” has multiple meanings. The original definition did not include malicious activity but rather meant modifying something to work better or differently. The FBI’s alert system allowed an outside user to sign up and push notification messages — effectively giving the bad guys a way to hack the email registration process to send out messages that appeared authentic. When thinking about cyber risk, it’s important to consider how you and your assets could be targets and how you might be used as a tool to attack others.
4. New bill sets ransomware attack response rules
There is a need for the federal government to assist in taking down the threat actors that are proliferating this ransomware epidemic. However, I am not sure this bill strikes an appropriate balance between data aggregation and law enforcement involvement and the existential threat to private industry that ransomware poses. The vast majority of ransomware demands are in excess of $100,000. The government delaying the approval of payment exceeding that amount could cause millions of dollars in additional business interruption damages for companies. – Rich Gatz, Claims Counsel
If you enjoyed this post, be sure to check our blog; the Risk Roundup runs Wednesdays in addition to more enlightening content we post related to the ever-evolving landscape of digital risk. Follow us on Twitter (@SolveCyberRisk), LinkedIn (Coalition Inc), and Youtube. If you have any suggestions for content that we should be adding to our reading list, let us know!








