Ransomware Myths Busted: How Cyber Insurance Impacts Payments

A blanket ban on ransomware payments is back on the agenda.
Proponents of a ransomware payment ban sometimes suggest the insurance industry is part of the problem. Some critics focus on crisis response, suggesting that insurance providers pay the ransom too often because the industry sees payment as an easy way out. Others focus on crisis prevention, arguing that policyholders view cyber insurance as a substitute for security investments.
Both arguments are out of touch with the reality of cyber insurance in 2024.
These myths distract from the reality that the insurance industry has the same mission as the policy establishment: Both want to prevent ransomware incidents and support breached entities' crisis response so they can resume operations quickly. The insurance industry is actively scaling up its ability to support under-resourced businesses' security efforts and, in doing so, simultaneously reinforcing government agency efforts and advancing security and resilience broadly.
The Cybersecurity and Infrastructure Security Agency (CISA) regularly communicates about vulnerabilities used by ransomware gangs, but lacks the resources to monitor millions of U.S. firms and help them mitigate issues. However, Coalition is doing exactly this with our policyholders. For example, we reached out to policyholders and helped them mitigate the Citrix Bleed vulnerability more than a month before mass exploitation by ransomware gangs led CISA and the Federal Bureau of Investigation (FBI) to issue a joint advisory on the matter.
When it comes to crisis response, the FBI helped Colonial Pipeline respond to a notorious ransomware incident in 2021, but federal agencies simply do not have the resources to scale up this support to all U.S. firms. This is exactly where cyber insurance comes into play: Our industry spends billions of dollars each year funding crisis-response work.
Some of this work involves compensating organizations for business interruption losses incurred while trying to recover, but it also means our industry is learning from breaches and incidents in real time. At Coalition, we use those insights to prevent policyholders from becoming future victims.
Misunderstandings about the role of cyber insurance in ransomware incidents have the potential to undermine opportunities for collaboration between insurers and policymakers. More importantly, these myths have the potential to drive policy responses that may be ineffective or, worse, exacerbate the problem policymakers seek to address.
With that in mind, let’s dispel some of the most common myths about cyber insurance and its impact on ransomware payments.
Myth 1: Cyber insurers pay the ransom to save money
The folk wisdom goes that cyber insurance providers prefer to pay ransoms because it’s cheaper than incurring the many other costs of business disruption. This myth is easy to dispel.
Cyber insurers routinely incur much higher incident costs than the initial ransom demand. This figure is based on NetDiligence’s curated dataset of nearly 10,000 cyber insurance claims across the industry between 2018 and 2023.
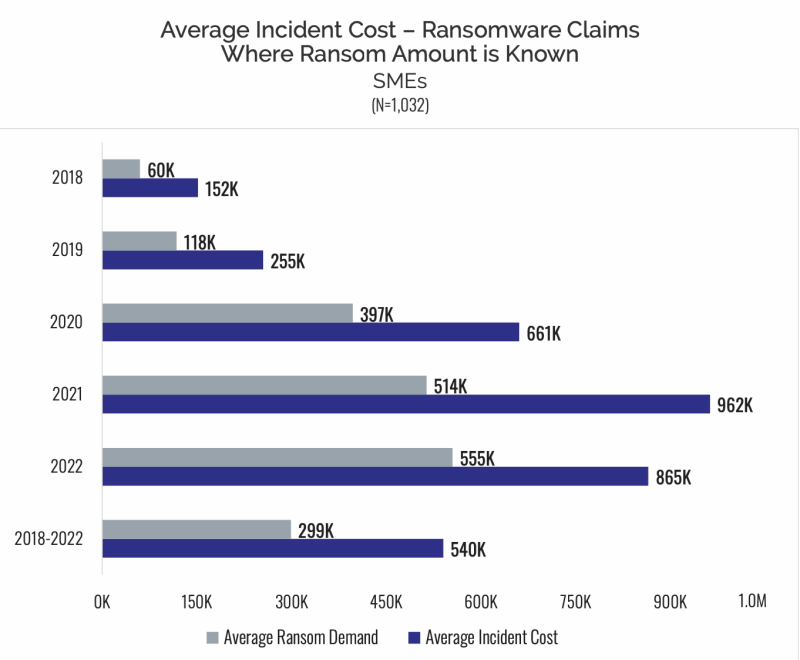
Average ransom demand compared to incident cost for SMEs. (Source: NetDiligence)
The numbers diverge because insurers end up spending more on crisis response and recovery expenses. For ransomware incidents, almost half of the claims costs (45%) went toward indemnifying businesses for lost income resulting from the incident. Digital forensics and incident response and legal practitioners represent another chunk of the incident cost — 56% across all small and medium-sized business claims, including non-ransomware.
Together, this data shows that a fraction of claims costs go toward ransom payments, precisely because insurance providers typically prioritize and fund strategies to avoid paying.
Myth 2: Cyber insurers are undermining resilience
Resilience to ransomware has changed over time. Consideration of a ransom payment ban would make more sense if businesses were at a reasonable level of cybersecurity maturity or if resilience were getting worse. This would be especially true if cyber insurance providers were making businesses more likely to pay the ransom — but data suggests this is not the case.
Coveware, a ransomware negotiation and recovery firm, has collected ransomware data dating back to 2019. In the early stages of the ransomware epidemic, around 80% of its clients paid the ransom. Over time, this number fell to a record low of 31%, a trend that suggests businesses are becoming more resilient over time.
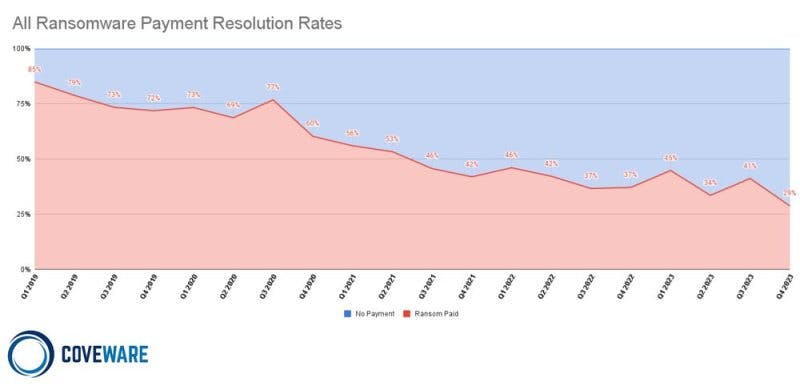
Ransomware incidents in which the victim paid the ransom. (Source: Coveware)
While this data appears to dispel the myth, not all of Coveware’s clients have cyber insurance. However, a recent academic study provides statistically significant evidence that “victims with insurance do not appear to be more inclined to pay the ransom.” This combination of industry and academic research does not support the idea that cyber insurers are reducing resilience over time.
The decline in ransom payments can also be seen in Coalition claims data. For non-zero ransomware claims, our policyholders paid a ransom 33% less often in the first half of 2023 than the first half of 2022. These figures exclude ransomware incidents in which Coalition resolved the incident before the policyholder made a claim. In the first half of 2023, 52% of reported events were handled at no cost to the policyholder — and, clearly, no ransoms were paid in these instances.
Myth 3: Cyber insurers have encouraged the ransomware epidemic
Ideally, we would have an answer to whether insurance has positively or negatively impacted ransomware. This is inherently difficult because we have no counter-factual world with a ransomware epidemic but no cyber insurance.
Nevertheless, the University of Kent and the Royal United Services Institute ran a multi-year study that concluded: “Cyber insurance is not fueling the ransomware epidemic by encouraging victims to pay ransoms, but it’s also not instilling ransom discipline in insureds across the market.”
This line of thought focuses on how cyber insurance providers shape negotiation strategies and finds the industry had a neutral impact. But insurers have also been actively reducing the rate of compromise, often alongside government agencies, in order to prevent infections that force the payment decision.
Vulnerability management is an obvious case study, given that exploited vulnerabilities were the leading cause of ransomware incidents in 2023. Both policymakers and cyber insurers invest resources in helping businesses to prioritize and address vulnerabilities, which can be seen in some “Celebrity CVEs” from 2023.
For example, Citrix published a security advisory about a vulnerability on October 10, 2023. Coalition immediately saw the potential risk, given that the vulnerability affected network-facing infrastructure. On the same day, we began notifying customers and getting analysts on calls to help policyholders to mitigate.

Citrix Bleed Timeline (Source: Coalition Cyber Threat Index 2024)
One week later, we learned that threat actors were exploiting the vulnerability, likely by reverse engineering the patch. Another month passed before we heard about mass exploitation by ransomware gangs, after which CISA published its advisory. By mitigating the vulnerability early, Coalition’s policyholders were largely able to avoid the decision of whether to pay a ransom.
This example speaks to the myth that insurance is a substitute for security. While that might be the case with more traditional insurers, Coalition and other actively engaged cyber insurance providers are continuously seeking to improve the risk profile of policyholders.
We believe our model is the future of cyber insurance, and the data speaks for itself: Coalition policyholders experience 64% fewer claims than industry average.
A ransomware payment ban is not the answer
Ultimately, cyber insurers and policymakers have the same mission. Both want to increase societal resilience but bring different resources and information in doing so.
Let us be clear: Coalition does not want policyholders to send money to ransomware gangs. The cyber insurance industry suffers when ransoms are reinvested into threat actor capabilities, like 0-day exploits, or spent on luxury cars that lure others into cybercrime. Both outcomes result in higher risk in the future — and we pay that cost in cyber insurance claims.
However, cyber insurance providers understand how disruptive ransom payment bans could be. Coalition sees the quantitative impact through forensic accounting reports submitted to claim business interruption expenses. These costs grow quickly and threaten the existence of a breached business. Coalition also sees the qualitative impact when our crisis responders work with policyholders to recover their business. Protracted recovery periods do not only impact the policyholder— they also impose significant costs on those who lose access to critical services.
Complex problems are rarely solved with binary solutions; ransomware is no different. A payment ban will limit options available to victims with little evidence doing so will end ransomware. In 2022, North Carolina banned state and local government agencies from paying ransoms, yet incidents affecting governments (and others) continued in 2023.
The government already has a policy lever (the Office of Foreign Assets Control) to ban payments to the most abhorrent ransomware gangs. We support and enforce that policy. In all other cases, we support policyholders in making the decision based on their specific circumstances.
The decision of whether to pay is a complex one involving multiple variables and made on a case-by-case basis. Paying every ransom is not the answer, but a payment ban is not a practical solution.








