A cyber analysis of a real world conflict
On February 24th 2022, Russia started an invasion of the Country of Ukraine. As Coalition both scans and has sensors on the internet (typically called honeypots) we decided to observe closely and document in this blog some of our findings or confirmation of facts related to this event.
Russian exposure
A hacking group called Network Battalion that has been compromising Russian infrastructure tweeted about a Gas compressor on February 27 being compromised by them, with a video being included with the tweet:
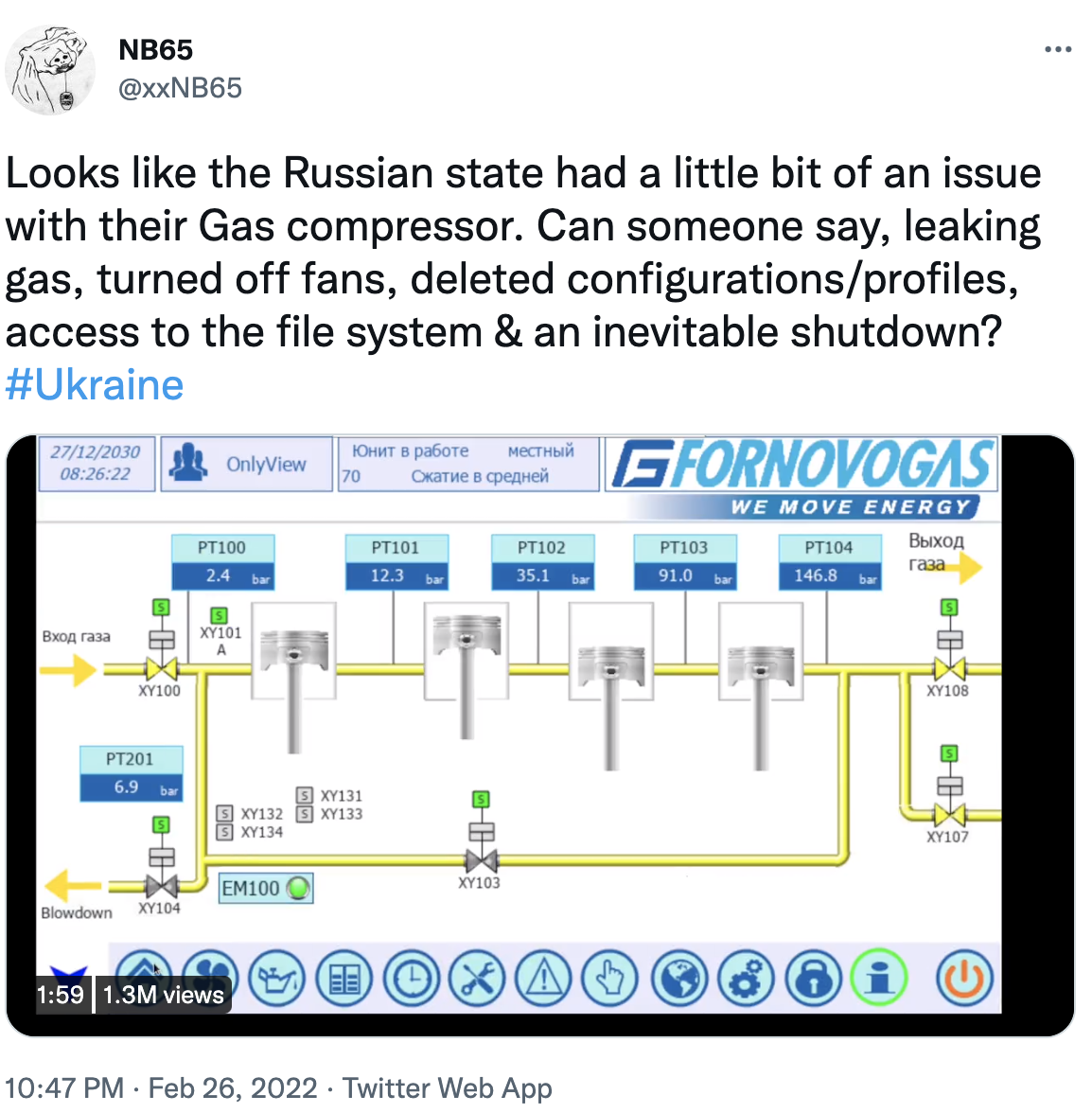
Some people questioned the veracity of this video, however looking at this video, we can see that some words that we can use in our image search feature, where images from RDP, VNC and X11 get OCR’ed by our system, we can confirm that this was indeed an system with VNC exposed without authentication to the internet for more than six months.
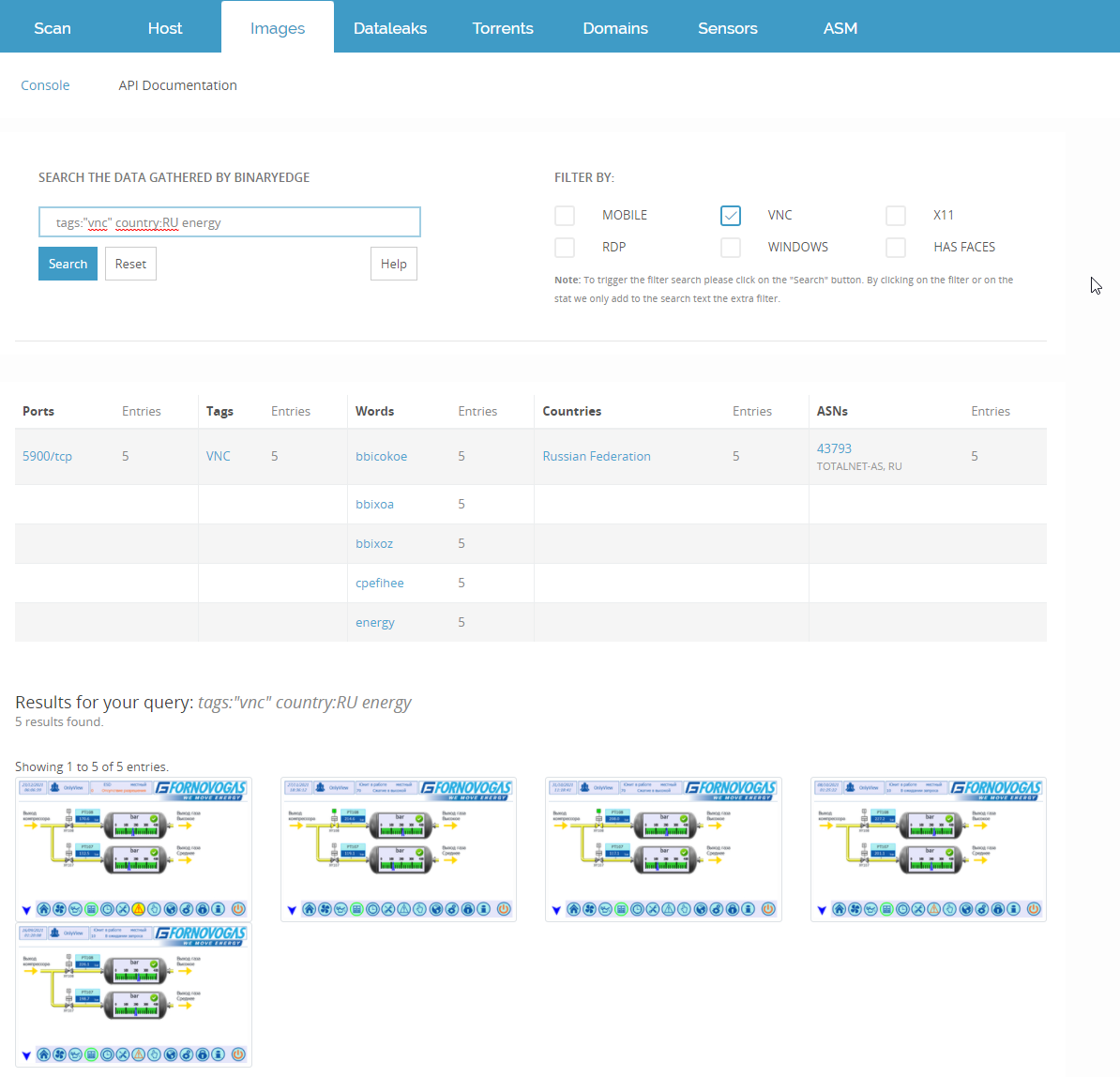
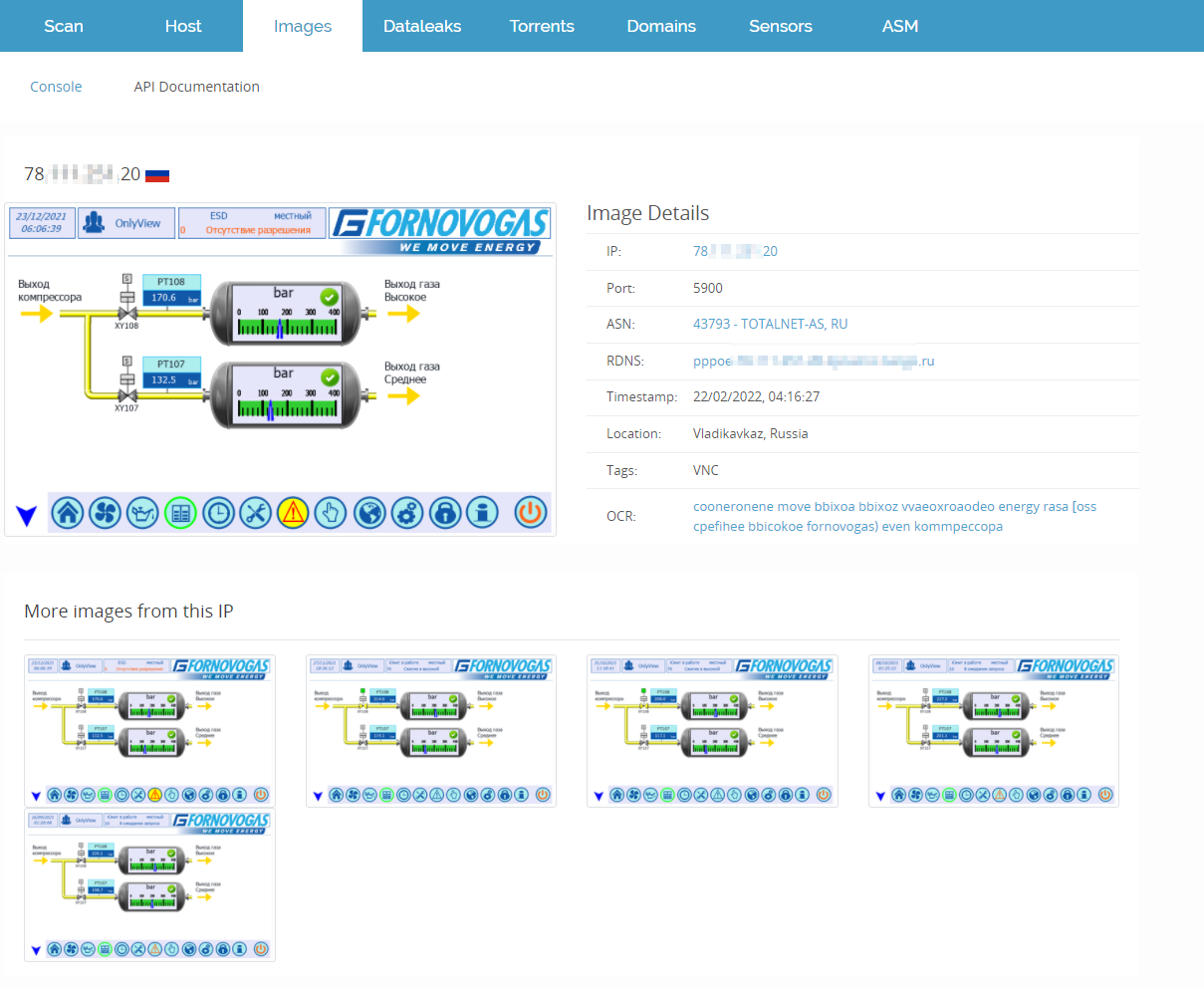
Looking at the Russian IP space, there are a few other interesting exposures, which we expect will see the same fate as this Gas compressor in the upcoming days (if they haven’t already been compromised).
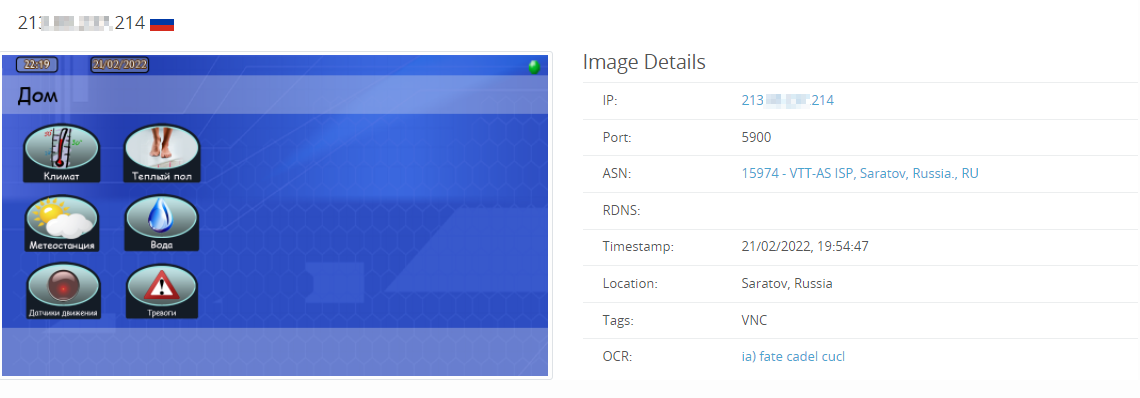
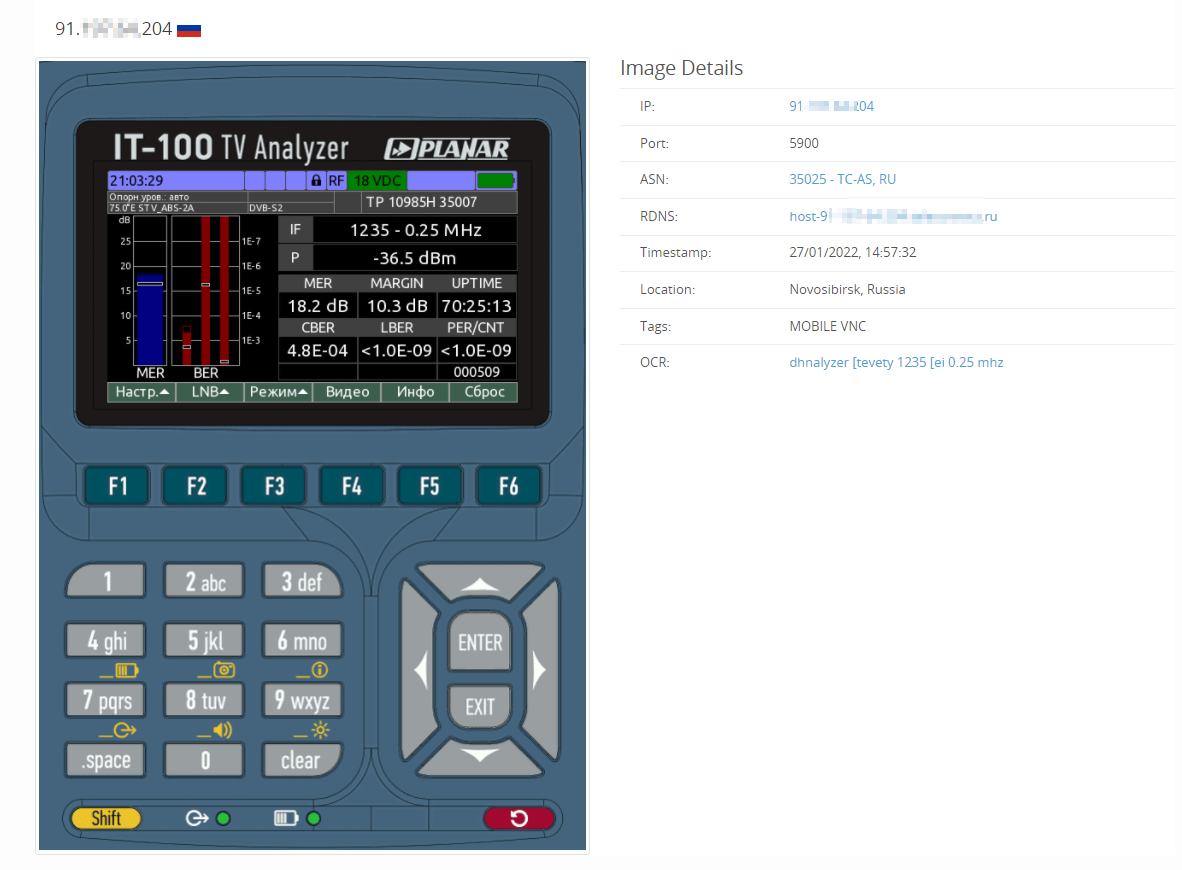
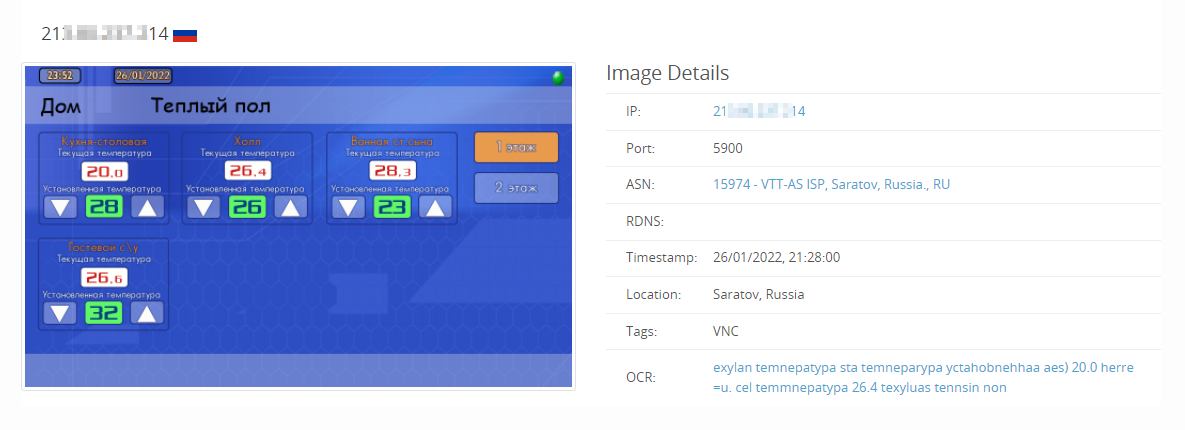
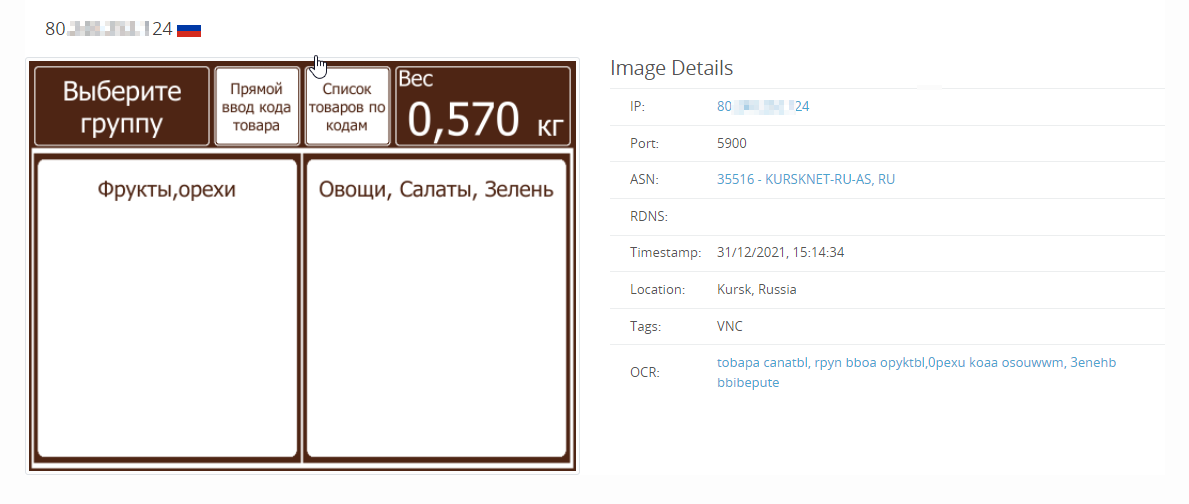
Looking at other types of exposures, we can see Russia has without authentication:
640 Elasticsearch
2312 MongoDB
1071 Redis
29 Cassandra
These databases already often get dumped by attackers so it won’t be surprising to see an even further increase in data being leaked from Russian systems. Some of it has already started, as we’ve seen multiple data leaks associated with the Russian government and entities appear in hacking forums.
When we actually start looking in depth at these exposures, we can start to see that actually some servers are already being hacked. An example is this server:
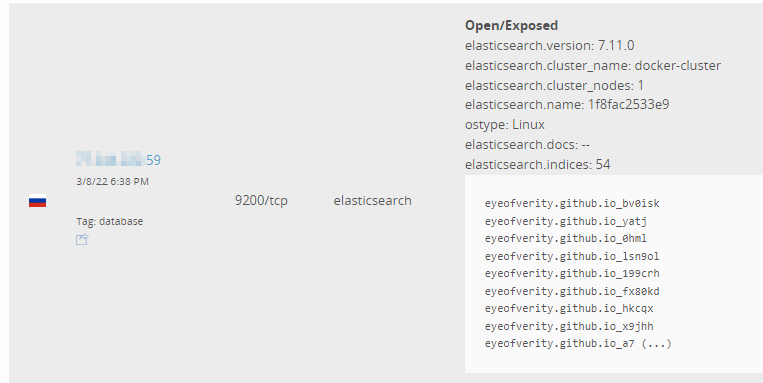
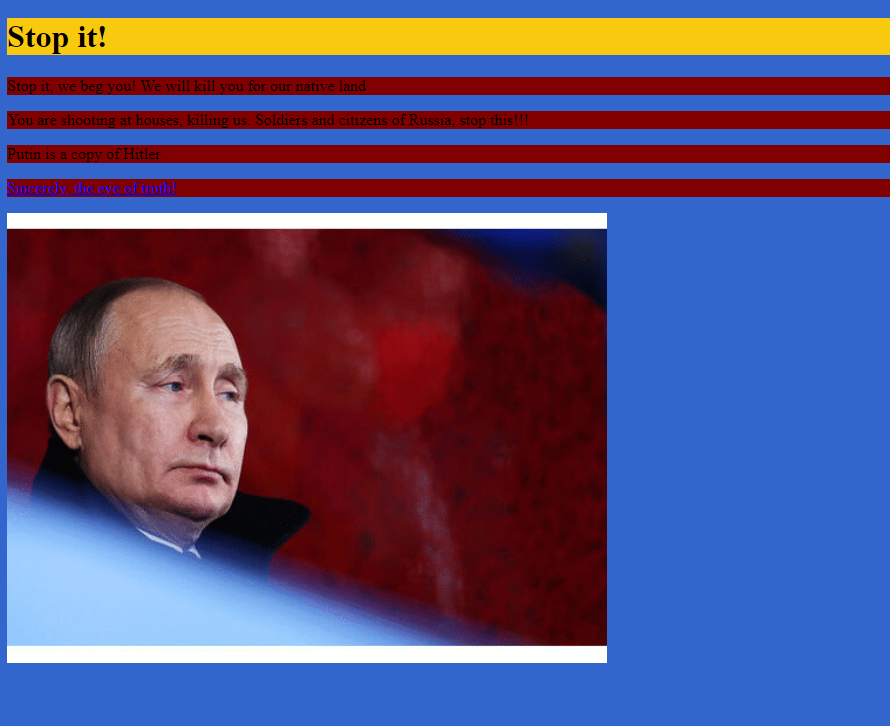
We can see the eyeofverity URL that is placed in the indices and upon visiting it, it is a dedicated slur website insulting Russia. At the time of this writing there are already 180 servers who have been hacked to deploy these indices.
Observed from our Russian sensors...
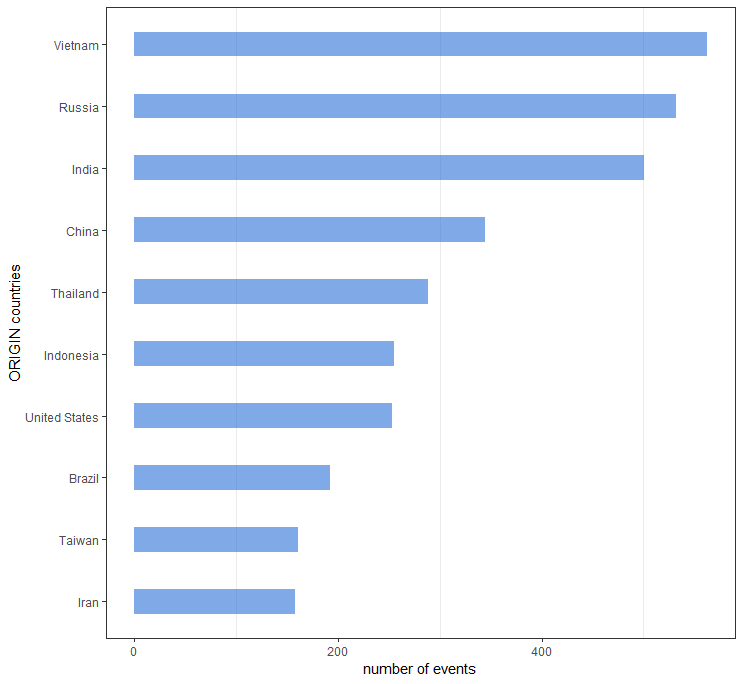
Coalition doesn’t just scan the internet, it also has a distributed network of sensors (typically called honeypots) which we use to understand attacker behavior and targeted exploitation. Out of 500.000 IP addresses we see across our sensor network, we detected 4842 targeting only our Russian honeypots. These 4842 IPs are associated with multiple countries however looking at the top ten, we identify the following countries:
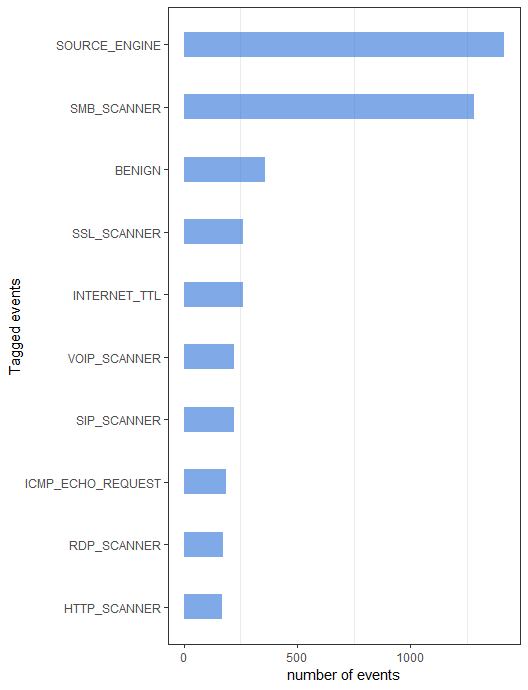
As we see events reach out to honeypots we dynamically assign them tags so that it's easier to know what they are associated with:
One interesting observation about our Russian Honeypots is how little we see them get hit with RDP events vs honeypots in other countries in the same timeframe (for some countries we observe x1000 with an elevated source of said scanning originating from RU).
One interesting finding is we detected one IP scanning our honeypot on the 6th of March for CVE-2022-26143 which is the vulnerability used for reflection and amplification on the TP-240 devices. Two days before this was announced (this IP now being owned by one of the actors listed in the coordinated disclosure).
But what about Ukraine?
We won’t be talking about any exposures in Ukraine, so we will focus on findings around our sensors and what is being scanned when targeting or being targeted from Ukraine space.
Overall we had not observed abnormal amount of scanning coming from Ukrainian IP space, however after the 14th, we started observing a specific set of IP addresses heavily scanning all of our sensors.
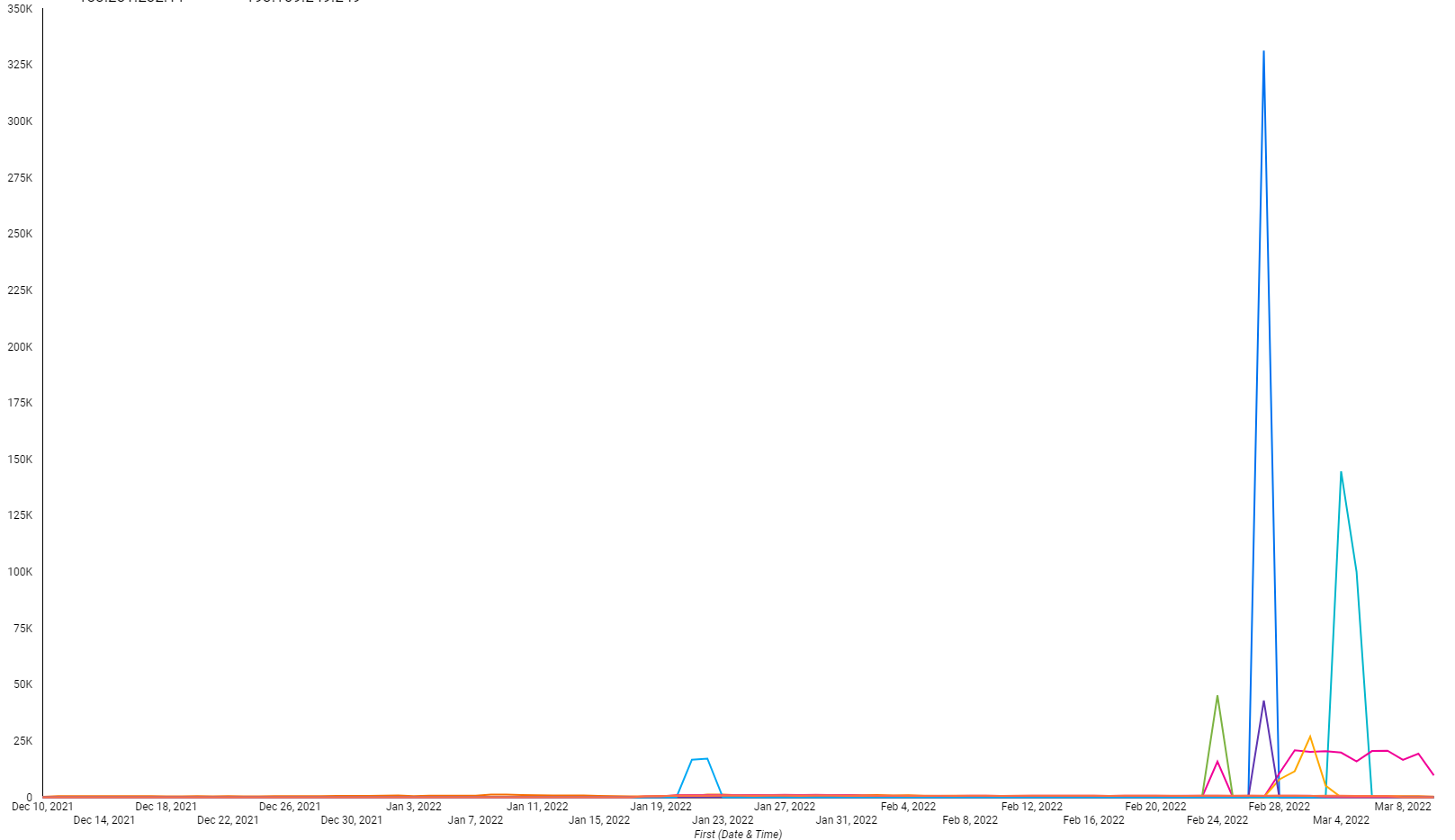
Initial thoughts were that potentially these could be routers being compromised and joining Mirai, however when looking at which traffic was classified as mirai vs what wasn’t we can observe that the spikes on scanning actually match with non-mirai traffic (blue line).
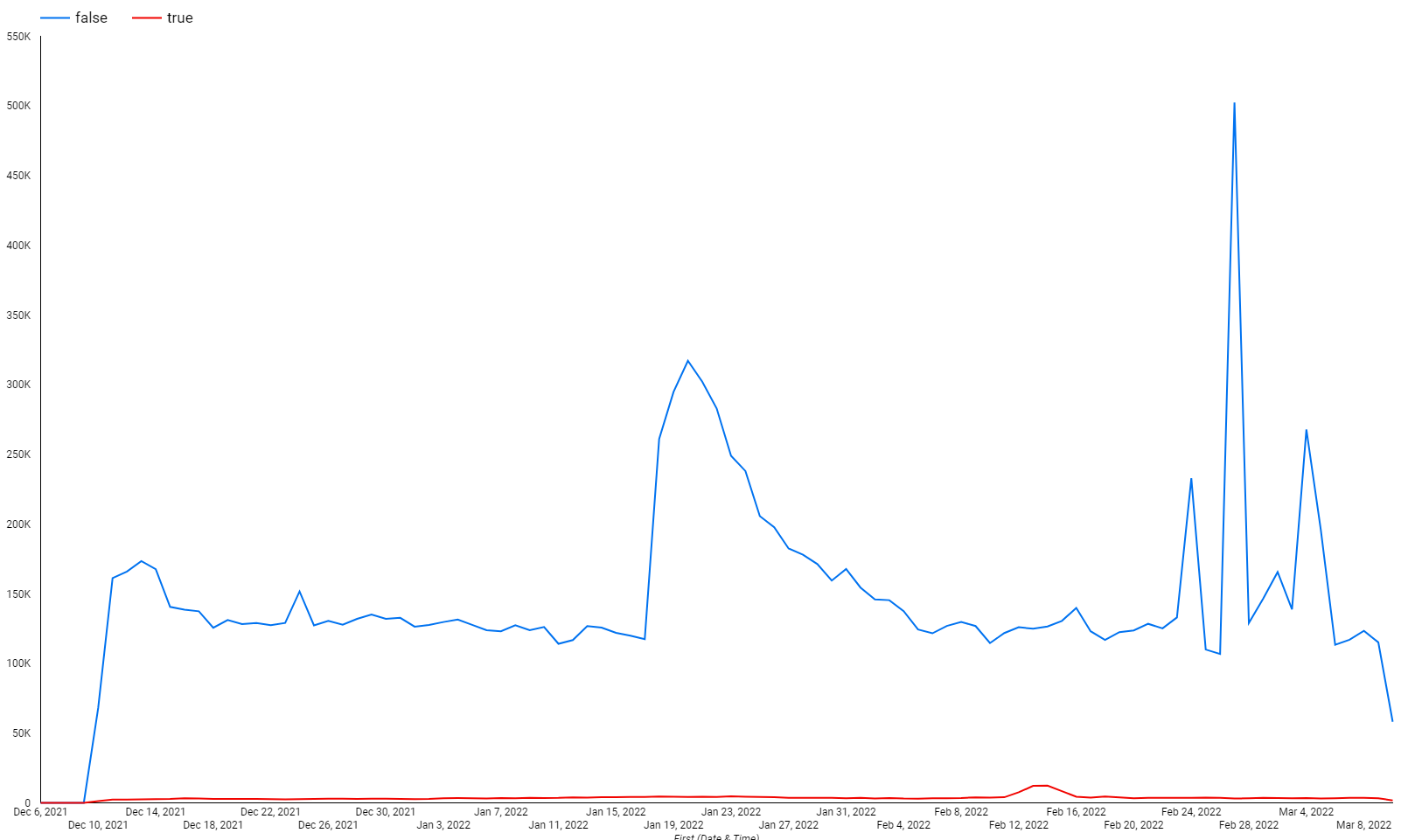
The type of scanning being done from Ukraine IP space is actually within the pattern we see with typical internet scanning, targeting RDP, SMB, HTTP. We’ve observed some groups making available open proxies for others to “help Ukraine”, so it is possible that someone is using those proxies to also do worldwide scanning and recon because although the scanning pattern is within baseline, the volume of scanning spikes after the 24th of February.
Looking at our own honeypots in Ukraine we observe an increased amount of UPNP scanning targeting Ukraine, also as previously untagged events, we see scanning on UDP traffic related to Mikrotik routers. When looking at other geolocations of our sensors we see an average of 60-100 events per day targeting Mikrotik, for Ukraine we’re seeing an average of 1,000 daily.
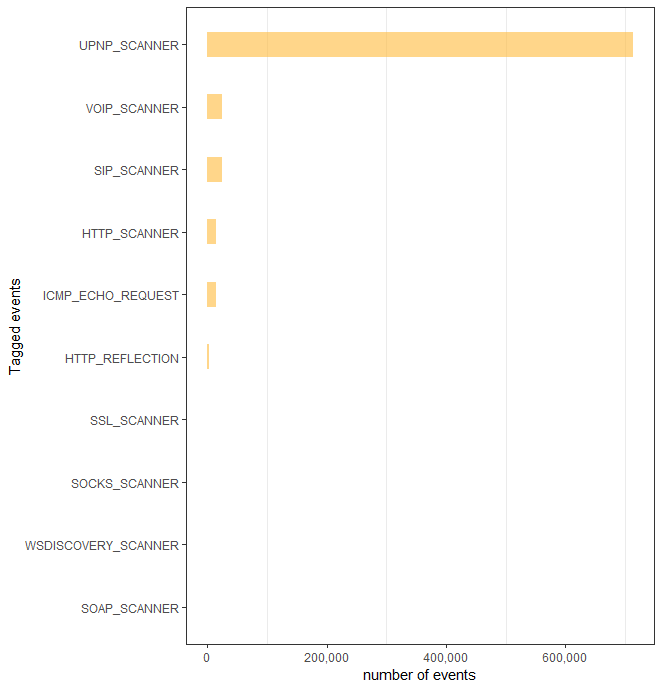
As time goes by we will write a second part where we drill further into the unique payloads we’re seeing targeting both countries or being used from the IP space of these two countries.
If you are a Ukrainian organization with a digital presence, a nonprofit or public interest organization anywhere in the world supporting human rights, civil society, democracy, journalism, the arts, Coalition will provide its cybersecurity tools and services to you for no cost with Operation Nightingale.








