August Risk Roundup: Solving ransomware requires timely info, key stakeholders, and a solid security program

Communication is vital as we navigate a cyber landscape rife with ransomware — which has become a viable business model for threat actors. As we increasingly focus on implementing solid cybersecurity programs, companies face scrutiny over the effectiveness of their alerts, their sales pitches, the exposure of their data, and how to successfully train and utilize their employees to prevent a cyber event.
1. Reactivate Clippy to help system administrators
Clippy’s AI can make up for the lack of intelligence in Microsoft’s security approach, like Exchange update tools that incorrectly say you’re up to date when, in reality, you're running an update level two years out of date. – Aaron Kraus, Security Engagement Manager
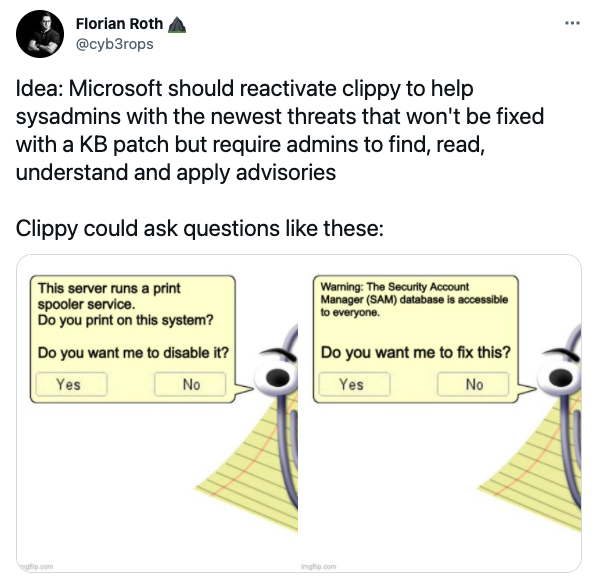
2. Be honest when selling ...
Messaging and delivery are essential to building a reputation. By now, we know that even the bad guys have figured this out since we’ve observed ransomware gangs deploy customer support and dedicated comms teams to increase their effectiveness. – Aaron Kraus, Security Engagement Manager
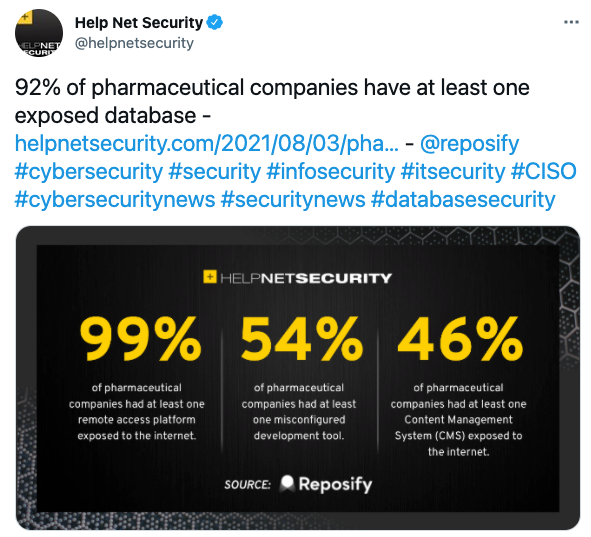
3. 92% of pharmaceutical companies have at least one exposed database
Misleading size, but the message is clear: pharmaceutical companies are struggling to protect their ecosystems from cyber attacks. Exposed services were found to be previously exploited in well-publicized attacks. It is crucial to have full visibility across your network that allows you to continuously monitor your network, your subsidiaries, and your third-party vendors’ cybersecurity. – Kirsten Mickelson, Claims Counsel
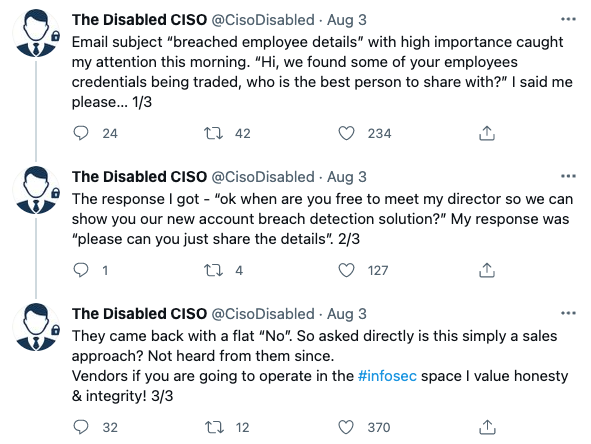
4. LockBit ransomware recruiting insiders to breach corporate networks
Yes, companies should be aware that a rogue employee or external vendor can be tempted by ransomware gangs and encrypt networks “accidentally.” However, this doesn’t seem likely for a few reasons. First, because of the likelihood of catching the rogue employee. Second, why would the ransomware gang want to share the proceeds when they know very well employees will do it for free by unknowingly clicking on malicious links. Companies should focus on training employees to be vigilant, enable MFA, segment data, test backups often, and ensure role-based network access and service level restriction. – Kirsten Mickelson, Claims Counsel
5. Angry Conti ransomware affiliate leaks gang's attack playbook
This is fantastic. We already have many of the files from the dumped toolkit after a complete forensic investigation but providing known bad IPs gives us a huge head start in the forensic search. We can assist clients in blocking these IPs off the bat; even if they migrate to new IPs, we now have some information from the inside, which always helps. We hope more information such as this continues to leak in the future, helping us all get ahead of ransomware. – Leeann Nicolo, Incident Response Lead
If you enjoyed this post be sure to check our blog weekly; the Risk Roundup runs Friday mornings in addition to more enlightening content we post related to the ever-evolving landscape of digital risk. Follow us on Twitter (@SolveCyberRisk) and LinkedIn (Coalition Inc). If you have any suggestions for content that we should be adding to our reading list, let us know!