How SSO & MFA Work in Tandem to Strengthen Your Cyber Defenses

When cyber attackers are looking to breach a business, their first step is often an attempt to gain access to the internal network. They do this by targeting exploitable technologies and force their way inside through software vulnerabilities, stolen credentials, or social engineering.
Once inside, attackers can move laterally from one system to another by escalating privileges, all the while looking for sensitive data that can be stolen or leveraged in a ransomware attack. In 2024, the average cost of a ransomware attack was $292,000 — and many of these attacks were carried out by attackers following a tried-and-true ransomware playbook:
58% of attacks exploited virtual private networks (VPNs) and firewalls
47% of attacks involved compromise credentials
27% of attacks used vulnerable software to deliver malware or steal data
Thus, the question for businesses becomes: How do I prevent attackers from gaining initial access to my network and what can be done to minimize the potential damage if a breach occurs?
Two of the most effective ways to protect against an attacker gaining initial access are single sign-on (SSO) and multi-factor authentication (MFA). Though these security controls serve different purposes, both can reduce your business’ risk of compromise by improving how employees authenticate into systems.
Understanding SSO and MFA — and how they work together as part of a defense in depth cybersecurity strategy — can help your businesses close one of the most commonly exploited doors into their network.
What is single sign-on?
SSO is a system that allows you to log in once with a single set of credentials to access multiple applications and services. Instead of remembering different usernames and passwords for every tool (email, file storage, cloud applications, etc.), you can authenticate once through a central identity provider (IdP).
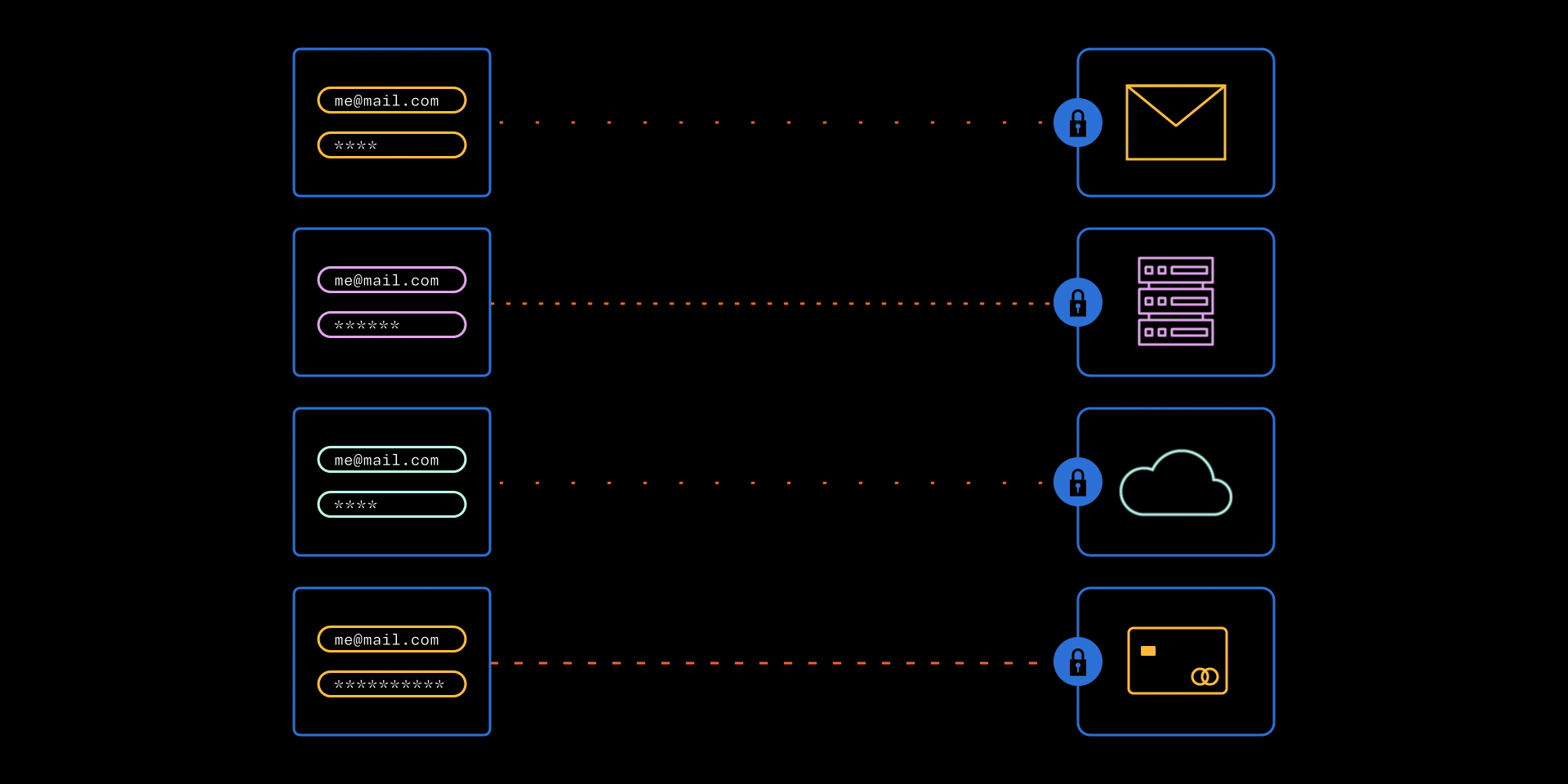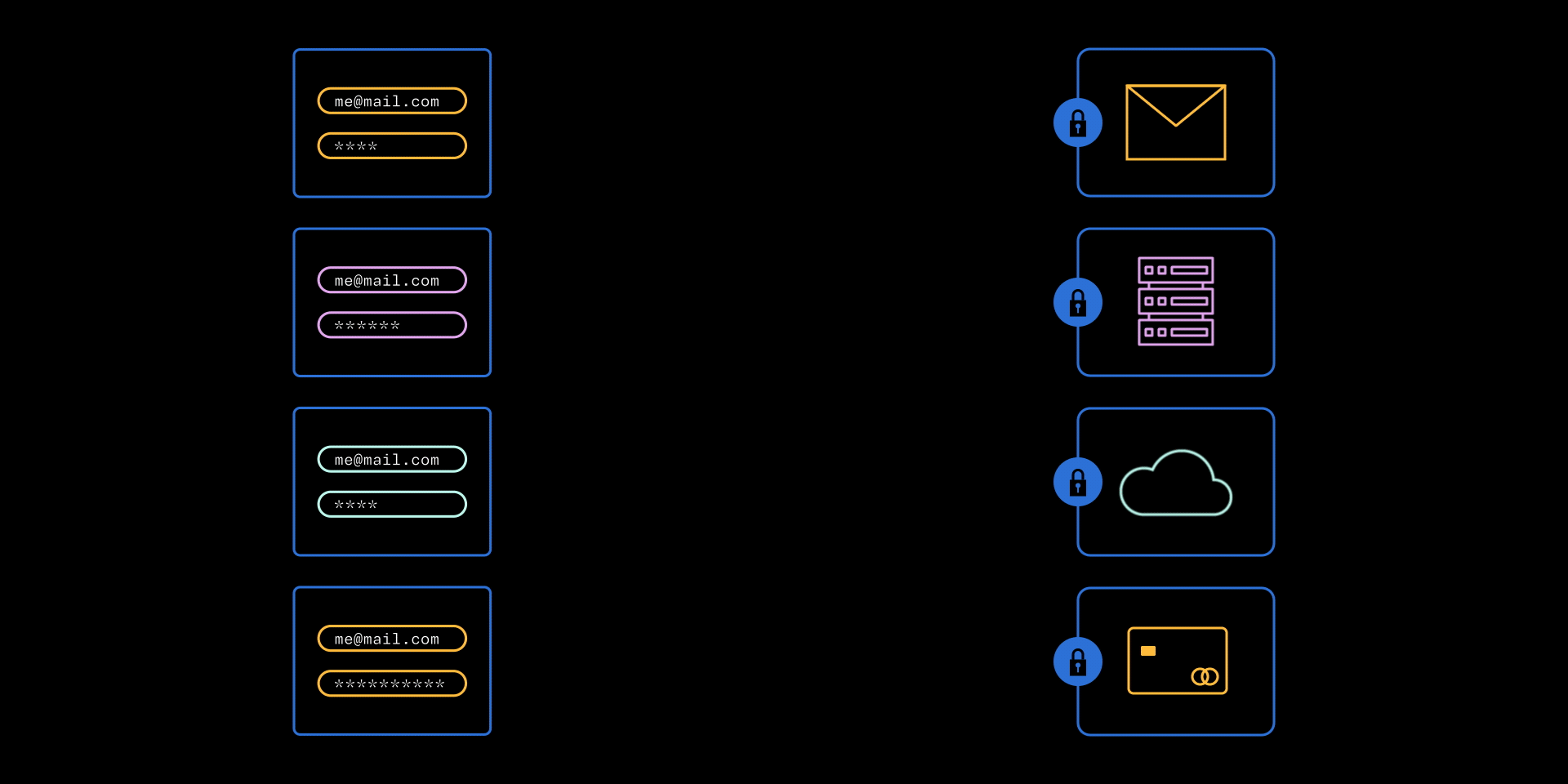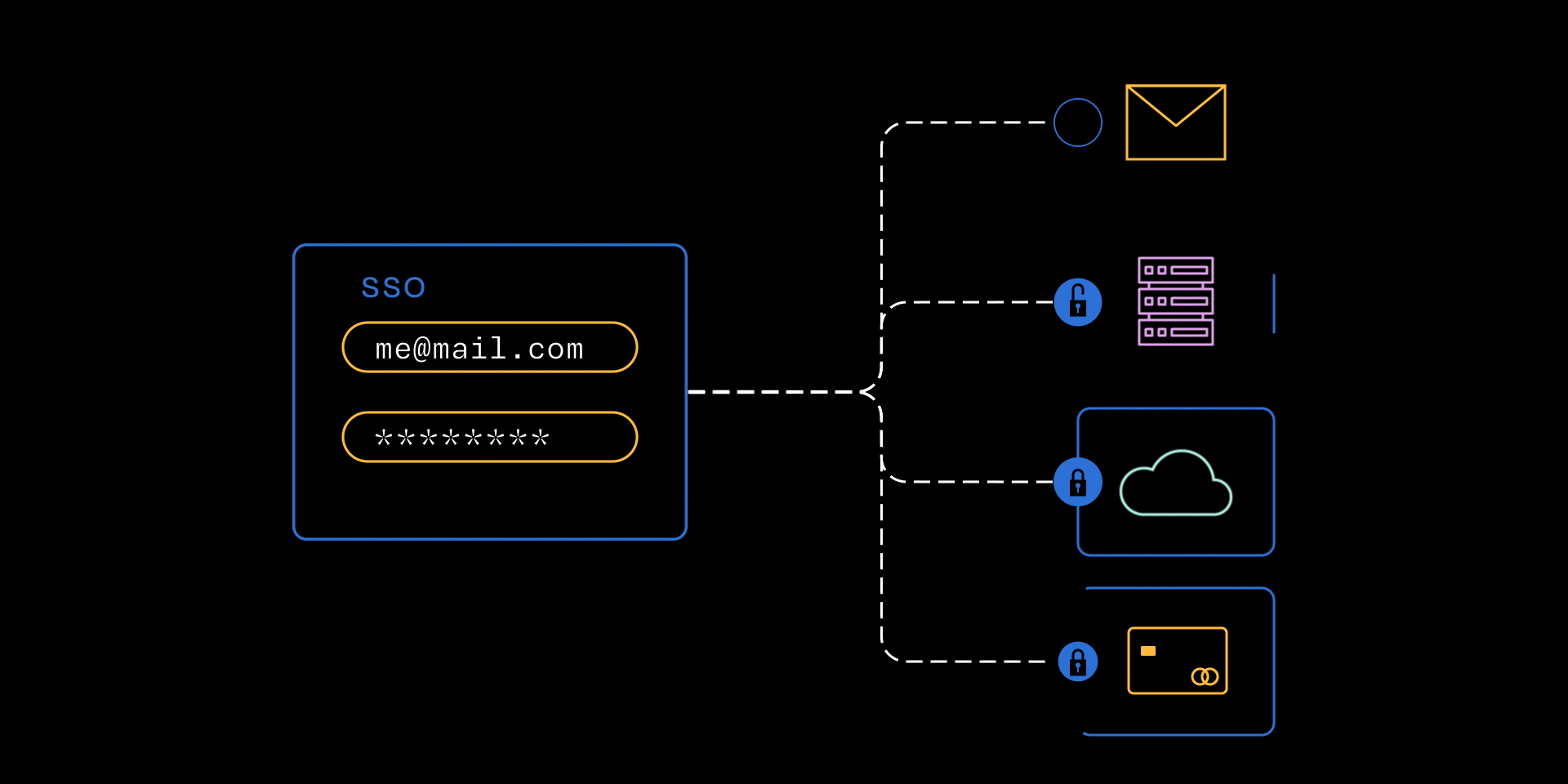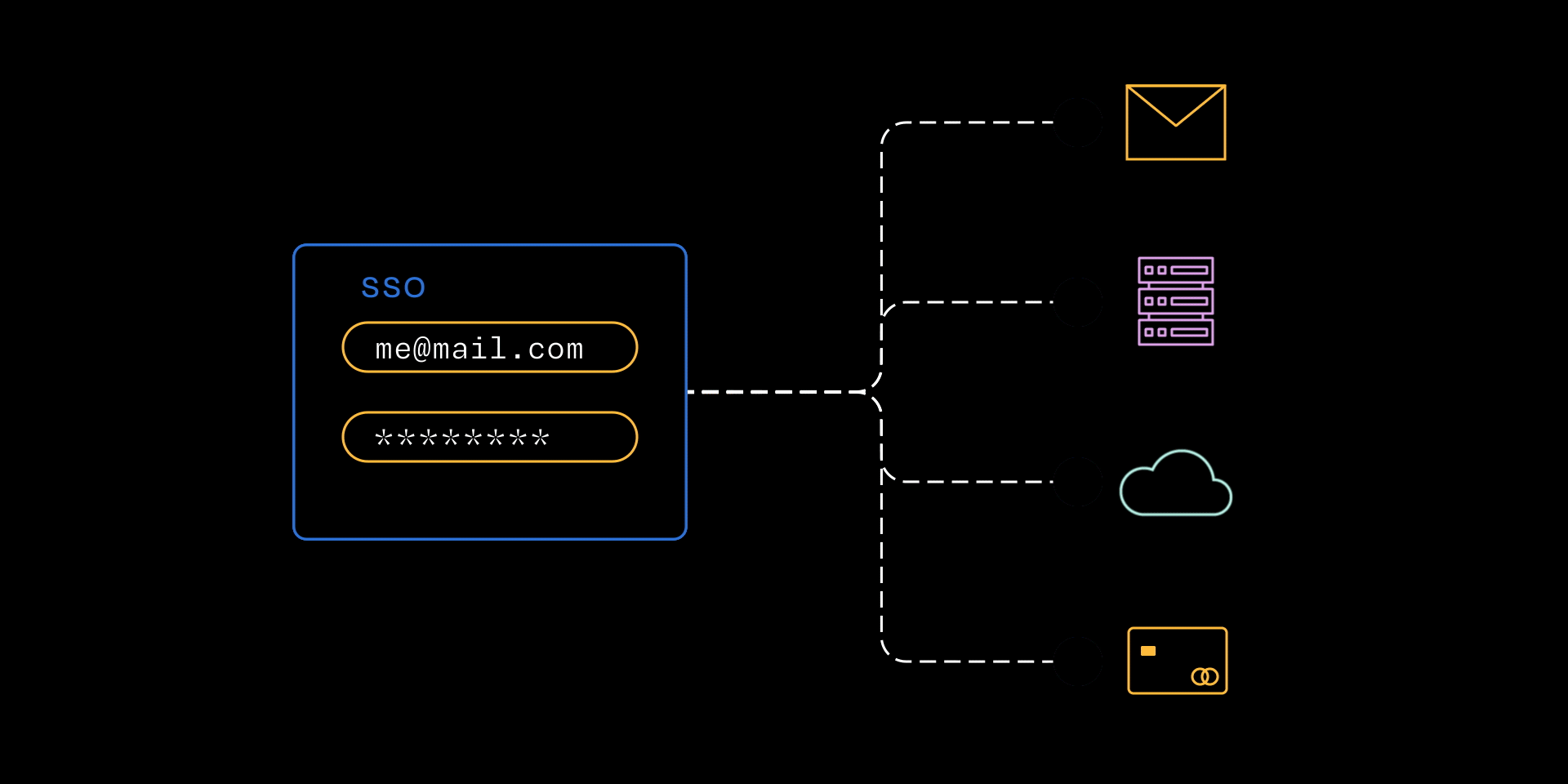
For example, by authenticating with your Google or Microsoft account, you get seamless access to tools like email, Zoom, file storage, and even Coalition Control® without the hassle of managing separate passwords.
SSO is a system that allows you to log in once with a single set of credentials to access multiple applications and services.
How SSO prevents initial access
Centralized authentication: All logins flow through one secure gateway, making it easier to monitor and detect suspicious activity.
Reduced password sprawl: With fewer passwords to manage, employees are less likely to reuse weak credentials across multiple platforms.
Simpler deprovisioning: When an employee leaves, disabling their single SSO account instantly cuts off access to all connected systems, reducing the risk of lingering accounts being abused.
Without SSO, employees may juggle multiple passwords, increasing the likelihood of weak, reused, or forgotten credentials. Attackers can exploit this through credential stuffing attacks, in which stolen passwords from one account are used to access others. Even worse, IT teams may overlook orphaned accounts on forgotten systems, leaving open doors for attackers to walk through undetected.
What is multi-factor authentication?
MFA adds an extra step to the login process by requiring at least two forms of verification, such as: something you know (password or PIN), something you have (smartphone), or something you are (fingerprint).
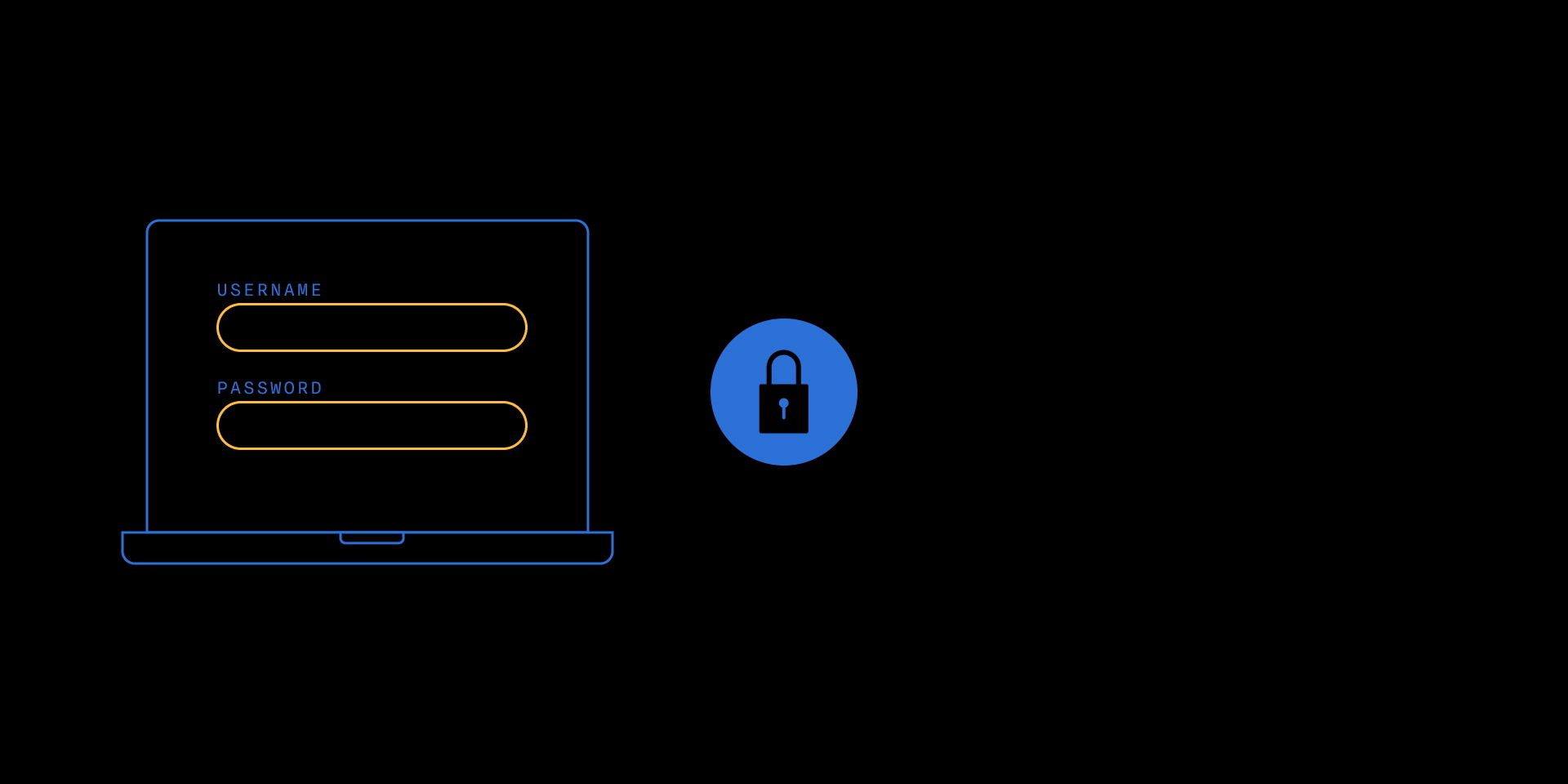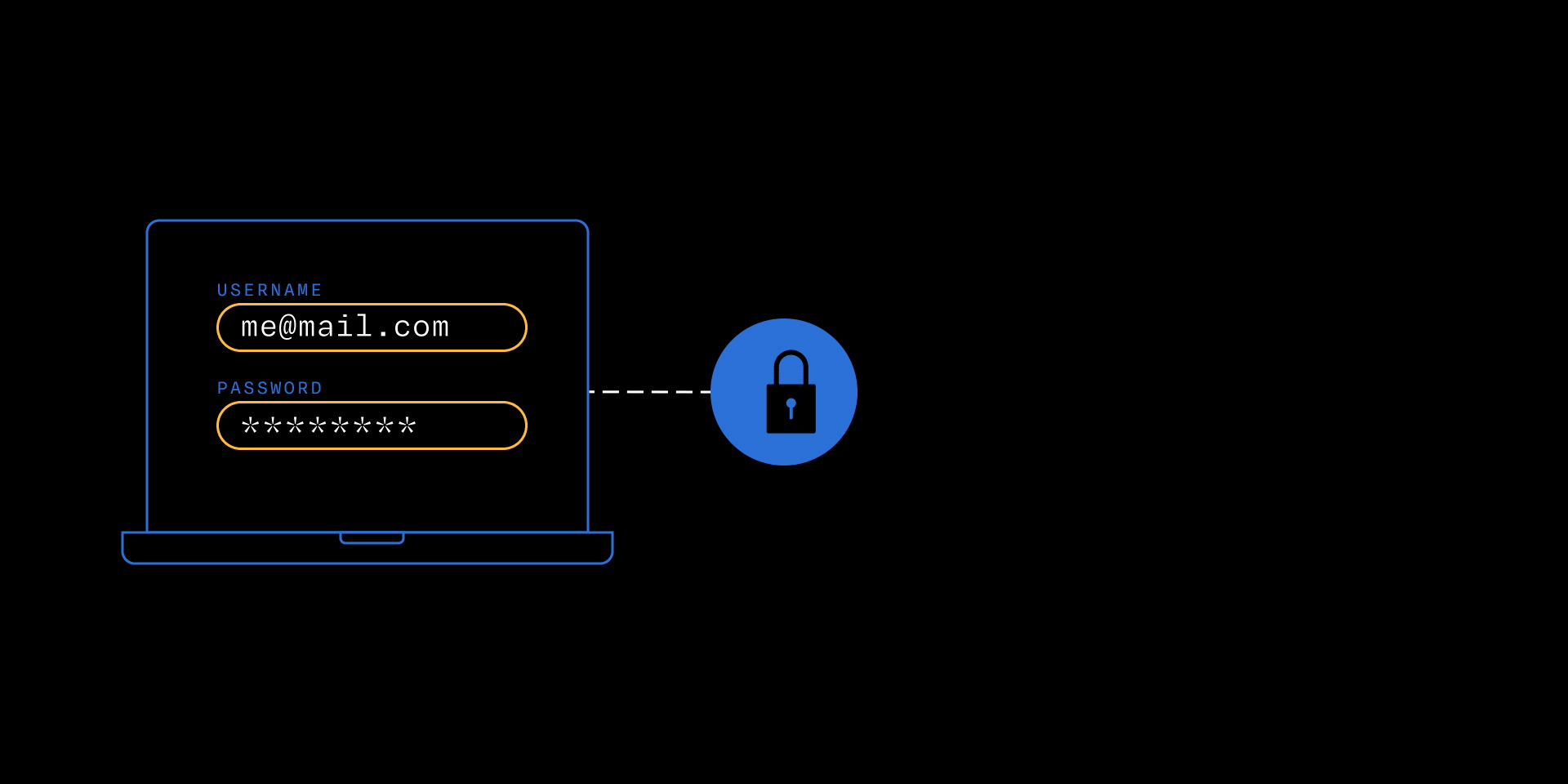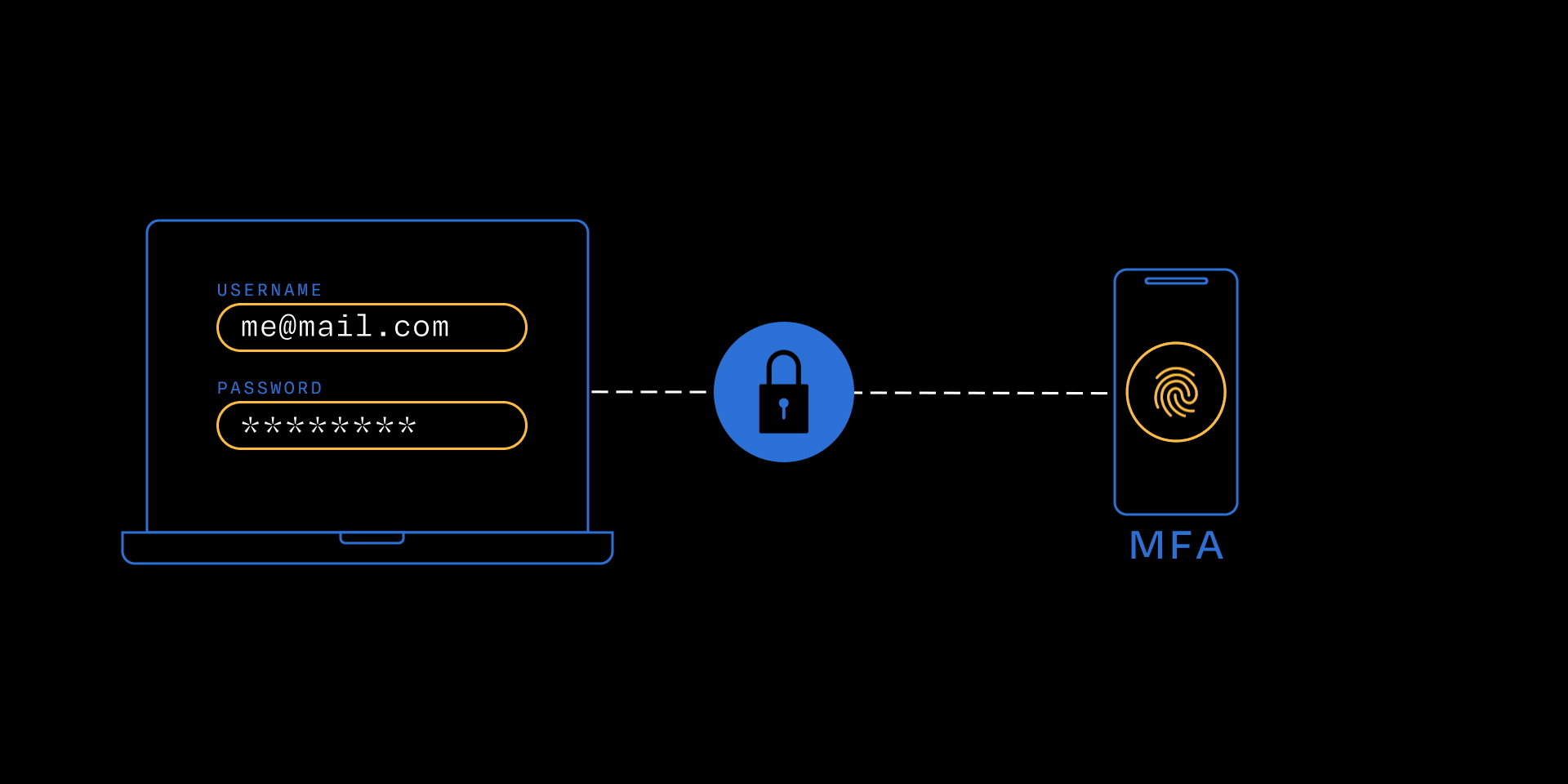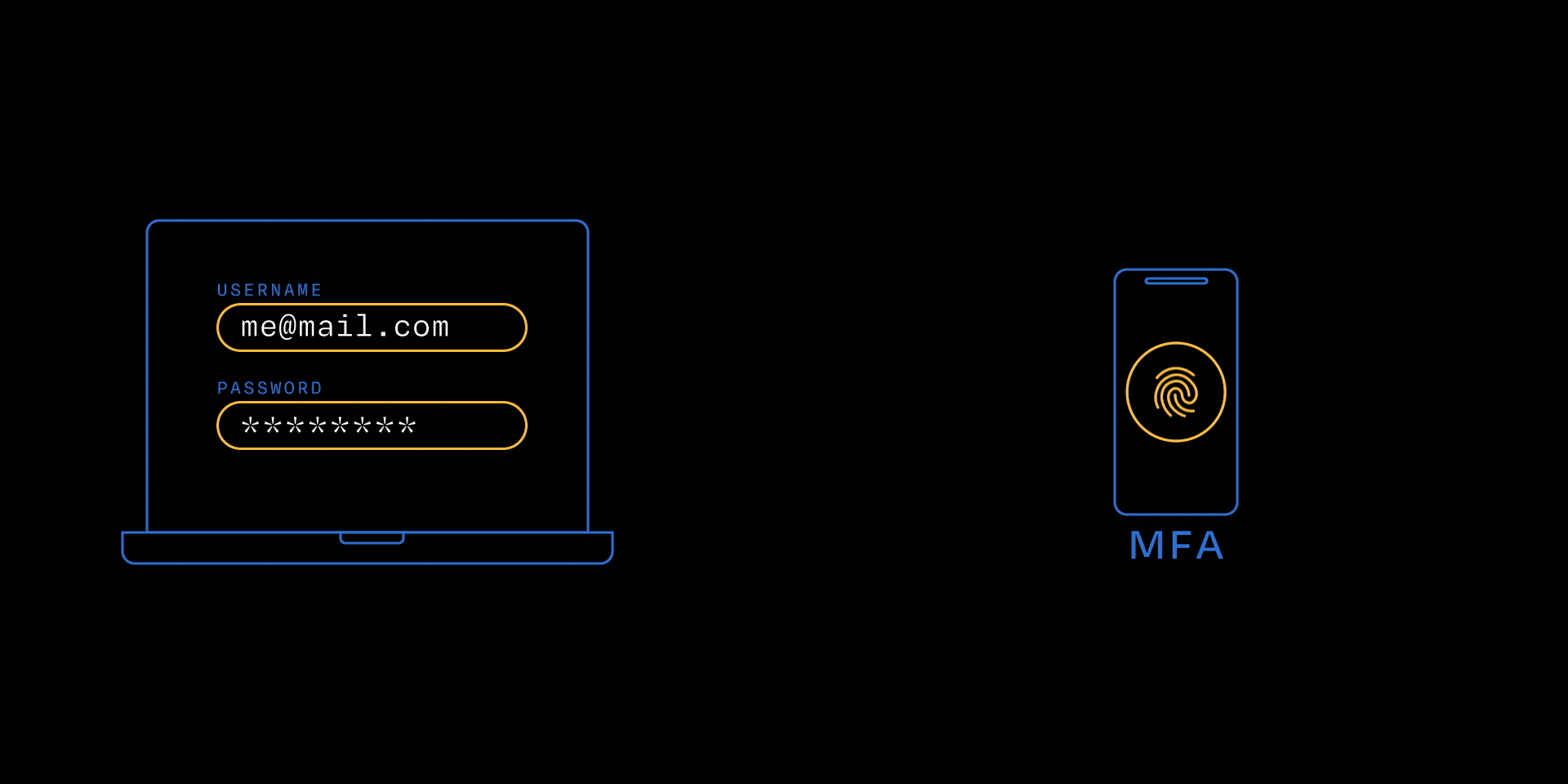
For example, after entering your password, you might receive a one-time code on your phone or approve a push notification in an authenticator app.
MFA adds an extra step to the login process by requiring at least two forms of verification.
How MFA prevents initial access
Stops password-only attacks: Even if an attacker steals or guesses a password, they can’t log in without the second factor.
Mitigates phishing impact: MFA can prevent stolen credentials from being immediately usable in most cases, reducing the fallout of successful phishing attempts.
Defends against credential leaks: Passwords exposed in breaches are far less dangerous when MFA is enabled.
Without MFA, stolen credentials are essentially a master key. A single successful phishing email or breach of another site can give attackers direct access to business systems, which is why credential theft remains one of the leading causes of initial compromise in cyber incidents.
How attackers exploit weak authentication
Cyber attackers often attempt to trick businesses’ employees into revealing credentials. In some cases, they’ll even buy account credentials on the dark web. Without SSO or MFA in place, attackers have multiple avenues to exploit:
Phishing for passwords: Users are tricked into logging into fake login pages. Without MFA, those stolen credentials can be used instantly.
Credential stuffing: Using automated tools, attackers test stolen passwords against multiple systems. Without SSO, there are more credentials to target.
Account sprawl: In non-SSO environments, old accounts on forgotten systems may never be disabled, becoming easy targets.
Password spraying: Trying common passwords across many accounts can quickly yield results when MFA isn’t a barrier.
Even a minor lapse, like one employee using the same weak password on multiple systems, can open the door to a major incident.
Without SSO or MFA in place, attackers have multiple avenues to exploit.
Better together: SSO and MFA
Individually, SSO and MFA provide strong protection. Together, they form a powerful access control strategy. When you integrate MFA with your SSO platform, users authenticate once through a secure, MFA-protected gateway, which means:
Every connected system benefits from MFA without having to configure it separately.
Security is consistent across cloud, on-premise, and hybrid environments.
Login fatigue is reduced since MFA prompts can be intelligently applied.
By making authentication strong and user-friendly, your business can reduce the likelihood of workarounds and shadow IT, both of which can undermine even the best security tools. This combination not only improves security but also enhances usability.
Employees face fewer logins, IT gains centralized visibility, and attackers find it much harder to get a foothold.
Simplify Coalition Control access with SSO
Sick of forgetting login information and resetting passwords?
You can use your Microsoft or Google account for seamless login to Coalition Control, no separate password required.
Simply click “Continue with Google” or “Continue with Microsoft” on the login page to get instant access.
Set Up SSO for Coalition Control now
EASILY SPOT & STOP CYBER THREATS IN ONE PLACE
Coalition Control
Take control of your cyber risk >







