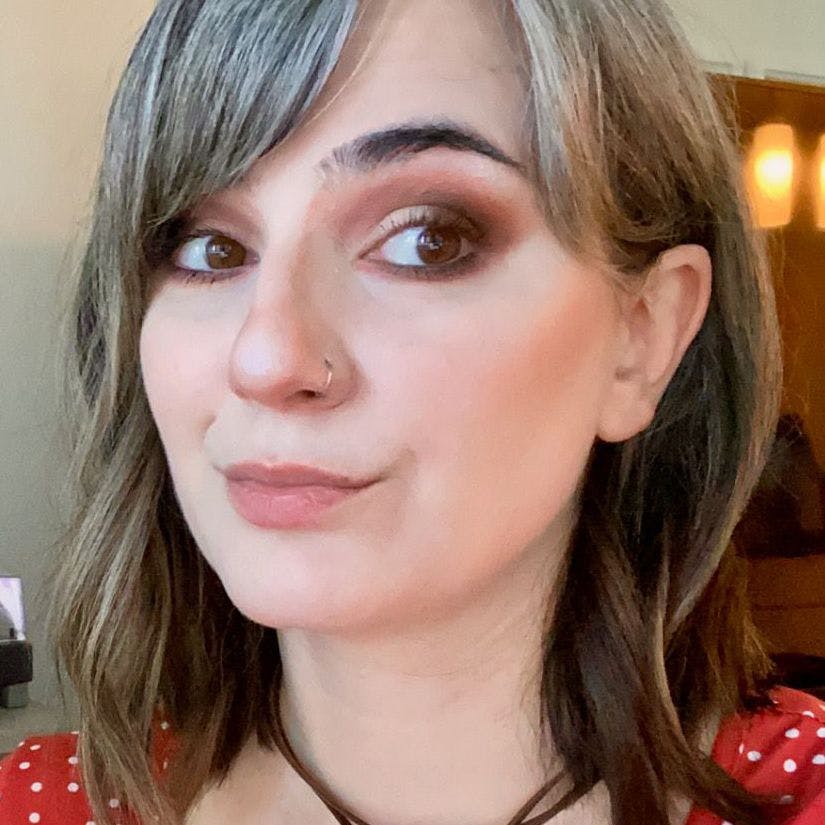We scanned the 5,000 fastest-growing companies: What we learned could benefit you

Coalition generates billions of scanning events every month and analyzes thousands of companies based on their internet-exposed assets — domains, subdomains, IP addresses, open ports — and what security misconfigurations or vulnerabilities exist on those assets. Using the Automated Scanning & Monitoring (ASM) feature available in Coalition Control, our integrated platform for monitoring and controlling cyber risk, we scanned (and scored!) the 5,000 fastest-growing companies to see what insights we may gain. These organizations are distributed across 45 industries, with revenues ranging from $2M to $8B.
What do you mean you scanned 5,000 companies?
It’s important to understand that we drew conclusions based on what information we could gather using outside-in enumeration and scanning techniques; no penetration testing or other red teaming was involved. In short, we viewed these companies the same way any malicious actor would.
Starting with an organization’s name, we collect thousands of data points split across multiple sections and types. These data points are compiled and scored using Coalition Control, our integrated risk management platform.
Insight 1: Unexpected risk scores
Our risk score system classifies different vulnerabilities and misconfigurations into four categories, low, medium, high, and critical, and then calculates a final risk score based on a combination of the different categories of vulnerabilities and exposed assets. Because Coalition deals with our policyholders end-to-end on their cybersecurity journey, we get a lot of visibility into the reliability of our scoring mechanisms. For example, suppose we classify an organization as not being high risk, and they experience a cybersecurity incident. In that case, we will feed all technical findings related to the incident remediation back to our threat intelligence and data collection teams, allowing us to adapt our scoring mechanism.
Looking back at the dataset of organizations in the 5,000 companies we analyzed, we saw two industries with a higher than average risk score. In fact, of all the industries we scanned, only two industries returned critical vulnerabilities: Equity Investment Instruments and Forestry & Paper. The third most vulnerable industry was Fixed Line Telecommunications.
As we mentioned before, Coalition Control is available to help your organization evaluate your cybersecurity risk and start building a security program.
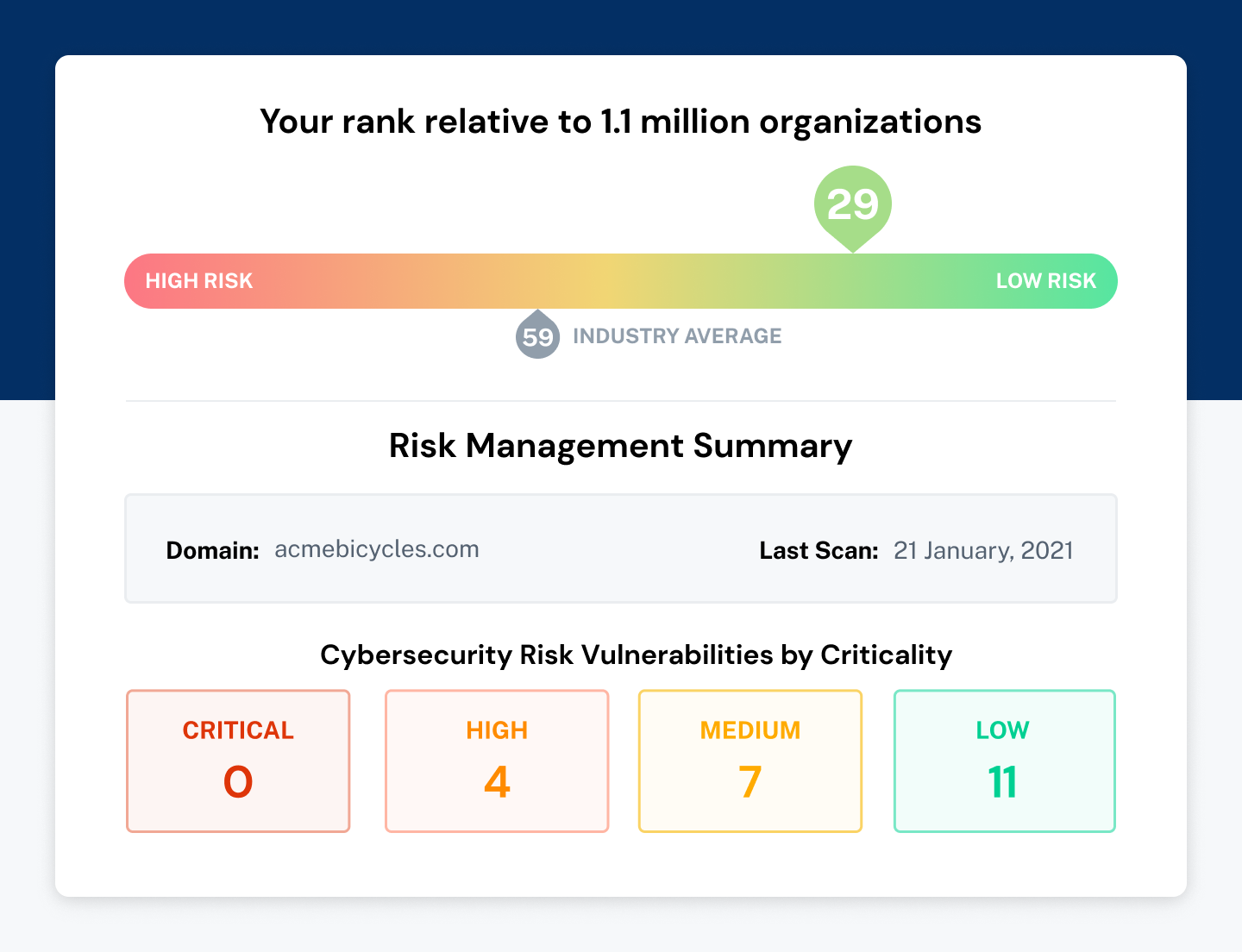
Upon logging into Coalition Control, you will see a risk ranking with a number — this scores your organization in relation to your industry peers. Below your risk ranking is our interactive Risk Management Summary. Here, you can sort through your vulnerabilities based on criticality and drill down into specific recommendations for remediation and the asset that is impacted.
Insight 2: More is more … risk
When we enumerate an organization, we discover lots of different types of assets. However, for this post, we focused exclusively on domains, sub-domains, and IP addresses.
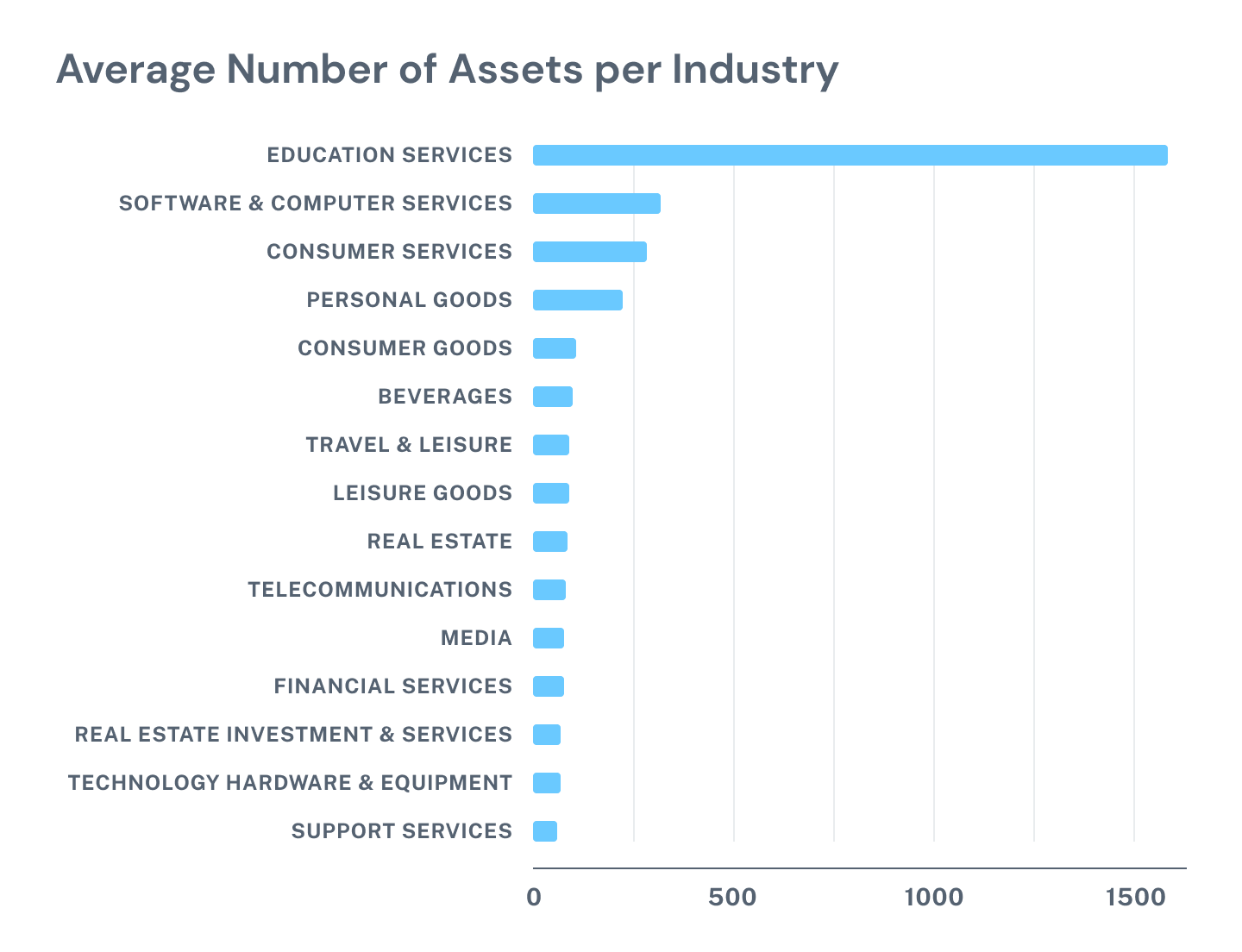
Educational Services, an industry well-known for owning large IP spaces, had significantly more assets than any other industry, with Software and Computer Services claiming the number two spot.
While the breakdown of assets makes sense, more assets still equate to more risk. We suggest applying a KonMari approach to your digital assets: remove unnecessary risk. We can almost guarantee a higher risk profile won’t bring any joy. With Control, you can discover what vulnerabilities your organization may have and take stock of what assets are internet-facing.
In the Control dashboard, you will find a breakout of Discovered Assets, which further breaks down into domains, IPs, apps, services, and hosting. From here, you can drill down and review any potential CVEs associated with each set of assets, allowing you to review your assets in totality and decide what risks are necessary, including those assets living in the cloud.
Insight 3: Everything really is in the cloud
While many cloud service providers exist, most organizations choose one of three providers: Amazon AWS, Google GCP, and Microsoft Azure. We’ve seen multiple companies struggling with understanding their security exposure, mostly because they struggle with asset management, and with cloud environments that allow for scalable computing, new assets can be added, removed, or modified, and data moved into those systems.
This is commonly referred to as shadow IT.
We found that overwhelmingly industries in the companies we evaluated utilized AWS at a substantially higher level. There was also a strong correlation between cloud provider usage and the number of IPs owned by an industry. We cannot assess whether or not the increase of IP addresses is due to shadow IT; however, we recommend organizations take stock of their cloud computing services and engage in shared responsibility with cloud providers. Coalition Control can assist with identifying errant cloud services that may have been spun up outside of the purview of their IT department.
Insight 4: Microsoft 365 vs. Google Workspace
By now, we would like to think most organizations are aware that email is not a secure form of communication. Business email compromise (BEC) was the initial point of entry for 60% of the claims reported to Coalition in 2020, a 67% increase from 2019.
Organizations that use Microsoft 365 are more than three times as likely to experience a business email compromise when compared to Gmail. - Coalition 2020 Claims Report
We observed a fairly equal distribution across all industries between Microsoft 365 and Google Workspace, with the exception of Support Services, which heavily favored Microsoft 365, and Media, which aligned itself with Google.
So now what?
With just your business email address, you can gain access to ASM in Coalition Control, which will provide your organization with ongoing monitoring and reporting of your attack surface — for free.
Not impressed with free? Attend a Control demo during Coalition Security Week.
In the demo, Coalition’s General Manager of Customer Security, Tiago Henriques, will introduce the Control platform and show how you can monitor your organization’s risk as well as your vendors.
Coalition Security Week will feature a series of co-hosted of webinars highlighting the capabilities of Coalition’s cybersecurity partners and the strength of a defense in depth security strategy for organizations of all sizes. For example, Coalition partner Curricula will host a fireside chat on the role of training in a risk management program — an especially critical function given that human error remains a root cause for many cybersecurity incidents.
Register to learn more about Coalition Control, or attend one of our Coalition Security Week webinars. There is no limit to the number of sessions you can attend, and should your availability change, the recap will be emailed to you at the conclusion of the event. See you there!