Cybersecurity education: Educate employees to throw back phishing attacks

Cyber threats are the great equalizer of our times — impacting all organizations and potentially turning employees from assets to risks. No technology is entirely secure, attack tactics and techniques are constantly evolving, and organizations assume some level of cyber risk when operating in a digitally connected world. To mitigate these risks, Coalition believes in incentivizing cybersecurity best practices. We have seen firsthand that technology solutions paired with incentives and support produce results: Coalition policyholders saw one-third as many claims as the broader cyber insurance market in 2020.
A key incentive every organization should undertake is enabling employees via training to recognize and report threats from phishing attacks, the most popular attack technique that hackers use to target their victims.
With great data comes great responsibility
Protecting company data is a shared responsibility for all employees, and most companies go to great lengths to underscore how good cybersecurity practices safeguard data. Businesses that operate in regulated industries, such as those dealing with healthcare, banking, or other financial data, have strict requirements to protect client and company data, and breaches or leaks can result in massive fines or regulatory action.
Employees and other users in the company, such as contractors or vendors, represent a combination of risk and protection when it comes to safeguarding critical information. One wrong click could welcome an attacker into the network, leading to a devastating cyber incident. It’s easy to view users as the greatest security weakness. But, if properly armed with tools, knowledge, and resources, these same users can be your greatest line of defense — a human firewall against phishing, ransomware, and malware.
Email phishing was the initial vector of attack for 48% of reported claims where this data was available. – Coalition Claims Report
Recognizing the tug of a phishing lure
Knowing how to properly defend against phishing attacks is crucial to the safety of your data and the data of your organization. Cyber attackers do their research; they craft phishing emails (a type of social engineering) to look legitimate, usually posing as a company or coworker you know and trust. Phishing emails often appear convincing to trick you into taking action, such as clicking a link or opening an attachment. A successful phishing email often creates a sense of urgency for the reader, and by applying just enough pressure, an otherwise diligent user can be tricked into making a mistake.
“If I can get into your network with a phishing email offering an employee a $20 Starbucks gift card, I’m not gonna blow a zero day I’ve been working on for the past 12 months.” – CEO Joshua Motta
Overwhelmingly, phishing emails and texts often employ the same type of request to trick you:
Attempts to alert you to suspicious activity or logins to your account.
Claiming there was an error with a regularly scheduled payment or an account change request — attackers have repeatedly capitalized on the COVID-19 pandemic to manipulate employees into fraudulent transfers.
Offers for coupons, free items, or a giveaway you don’t remember entering, which are often too good to be true.
Spearphishing or whaling attacks target specific individuals, often executives at an organization.
Phishing can lead to business email compromise attacks, where hackers take over the mailbox of a specific individual. Once compromised, this email is often used to perpetuate further attacks since the email belongs to a known and usually trusted person.
In addition to phishing emails, attackers will sometimes utilize phishing phone calls (an act referred to as voice phishing or vishing) posing as tech support, a company, or a government agency. Common scams include receiving an offer to purchase an extended warranty or a warning that your computer is infected and you must urgently install a program or allow the caller to remote in. Phishing can also take the form of SMS messages, although these smishing attacks largely focus on convincing the reader to click a link.
Probably the most important thing to understand about phishing is this: anyone can be a target. Organizations of any size and industry are targeted daily by hackers in hopes of an employee falling victim to a phish. Attackers cast a wide net in the hopes of catching at least a few victims.
Toss back bad phish by focusing on people, processes, technology
Understanding that phishing scams are targeted, sophisticated, and meant to convey a sense of urgency leaves a resounding question: what is the right combination of tools and incentives to help employees pause and recognize a phishing email as a scam? Curricula CEO Nick Santora (CISA, CISSP) believes the key to improving security awareness is getting employees to care. To foster caring, focus on employees first: provide cybersecurity awareness training that isn’t too technical, too dull, and solicit employee feedback. Ideally, this will empower employees to notice when processes or technologies meant to thwart attackers are failing or malfunctioning, removing human failure as a risk factor.
Once an employee identifies that an email or phone call is likely fraudulent, they may be left wondering how to respond or report the scam:
Don’t click links is combating phishing 101 — get in the habit of hovering over links to examine the URL.
Verify the sender’s email address and take note of any misspellings or inconsistencies.
Emails should be used as a notification system, not a shortcut — be suspicious of emails that convey a sense of urgency.
Always report suspicious emails, instant messages, or text messages to an incident response team (likely part of the corporate help desk).
Utilize a two-step verification process for any requests to change payment information, such as callbacks to verified numbers.
Never open unexpected attachments, especially when you didn’t request them.
Think before you act, and contact the sender directly to ensure authenticity using a known good phone number or email address.
The quicker an organization’s IT security team can spot a phishing attack, the better. Employees can be empowered to work together to recognize and report phishing attacks to ensure hackers are blocked.
Partner spotlight: Curricula security awareness training
With a proven security awareness training program, companies can dramatically reduce their risk exposure and empower their employees to cast back unwanted phish. Coalition security partner Curricula offers security awareness training to prepare employees. Instead of “death by PowerPoint,” Curricula uses behavioral science techniques, like storytelling and a diverse cast of characters. One such character is DeeDee, a five-year-old hacker who delights in tricking users into surrendering critical information.
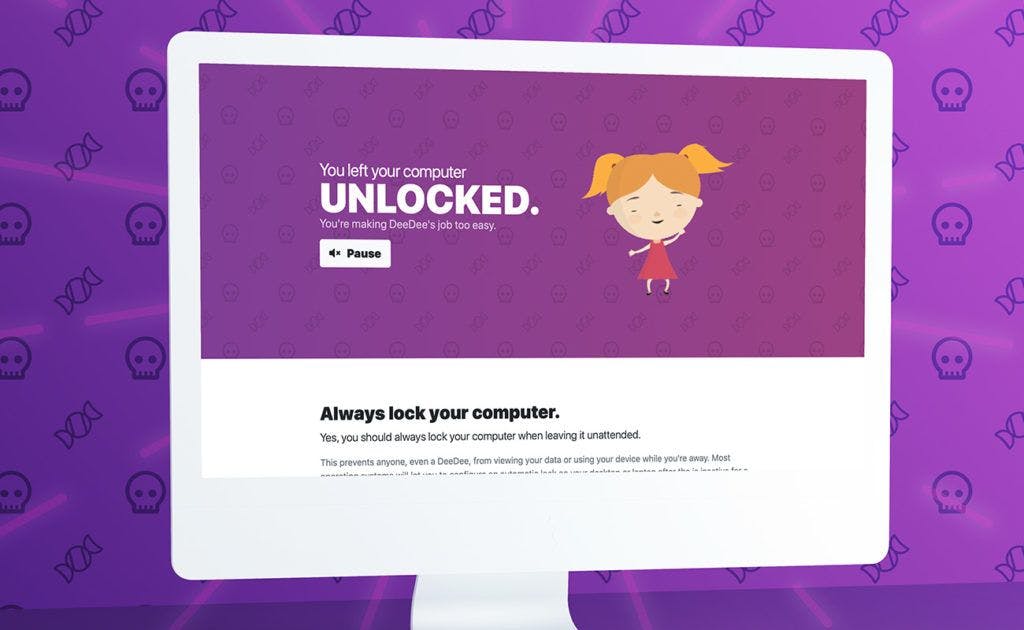
Security awareness training only matters if employees can remember and recall the information to use in real-world scenarios, which is why Curricula also offers simulated phishing tests that help train policyholders to dodge real-world attacks. Clicking on bogus links will direct users to a Curricula training module, and admins can view click rates on each campaign through their Curricula dashboard.
Cybersecurity events will happen, but they don’t have to transform into cybersecurity incidents, which is why organizations need cybersecurity awareness training. Coalition policyholders can log in to their policyholder dashboard and take advantage of free Curricula licenses to train their employees to remember and react to phishing attempts.
Additionally, Coalition’s cybersecurity guide outlines the basic tenets of a cybersecurity program — a critical factor in reducing your organization’s cyber risk. You can also download the full H1 2021 Cyber Insurance Claims Report to learn more about the cyber trends impacting all organizations and our predictions for the remainder of 2021.