JARM and SMB: New modules and data for comprehensive scanning

We are always looking for new ways to expand the types of data, services, and vulnerabilities we scan for in order to improve our customer's cybersecurity. This week, we've added two new modules to the scanning pipeline, which will also be used in our Attack Surface Monitoring (ASM).
JARM
Three days ago, the Salesforce security team shared a new type of Transport Layer Security (TLS) fingerprinting — JARM.
Scanning with JARM provides the ability to identify and group malicious servers on the Internet. It allows the generation of unique signatures for services that use TLS for communication, which means it can be a new signal to help identify which services are exposed on an IP address.
JARM fingerprints can be used to:
Quickly verify that all servers in a group have the same TLS configuration.
Group disparate servers on the internet by configuration, identifying that a server may belong to Google vs. Salesforce vs. Apple, for example.
Identify default applications or infrastructure.
Identify malware command and control infrastructure and other malicious servers on the Internet.
Salesforce made the announcement in a blog post titled, "Easily Identify Malicious Servers on the Internet with JARM." After reading it, we knew it was a powerful tool that we needed to start scanning with, so the team went to work.
24 hours after the tool was released, it was deployed on our scanning engine as a module available to all enterprise customers (who can also use it in their custom scans). A scan is ongoing to generate a JARM hash for every single service we have ever seen with SSL.
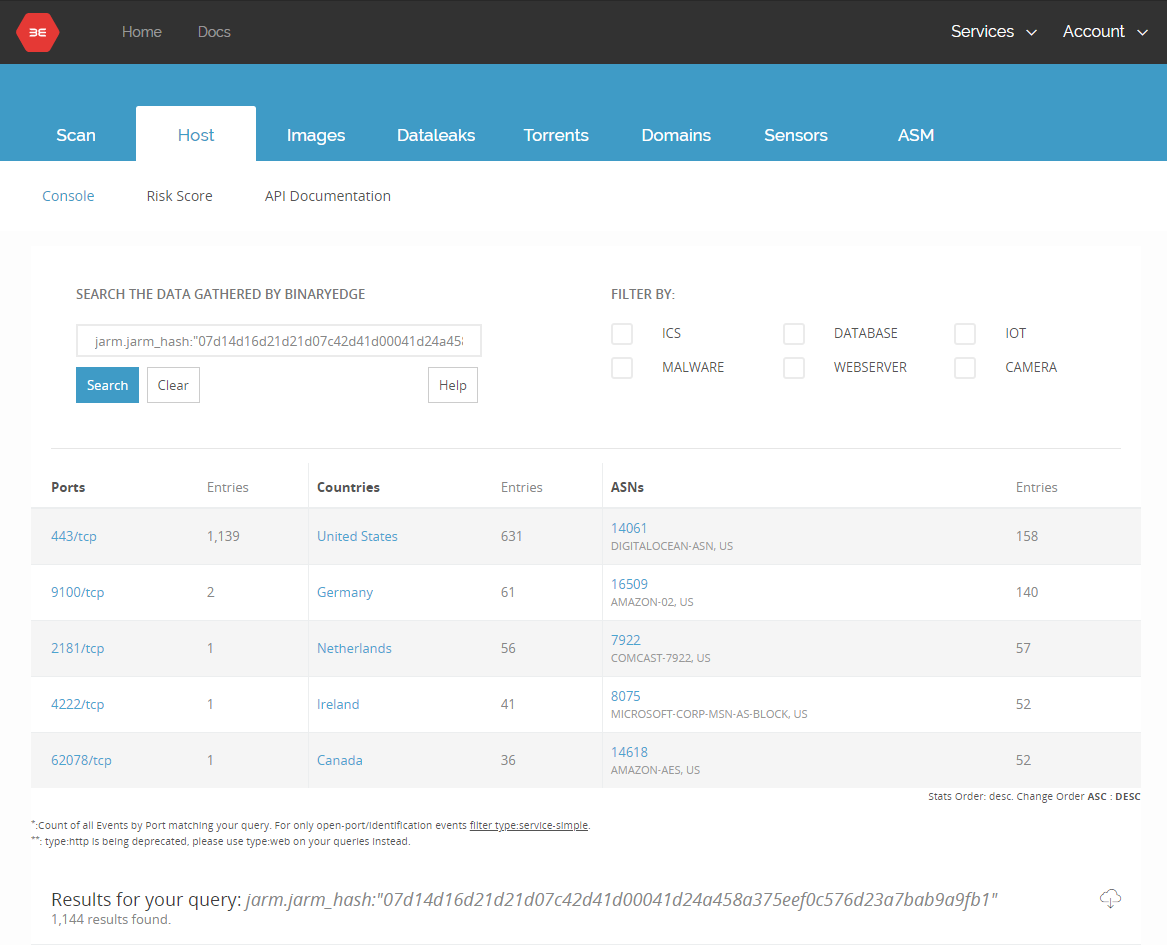
The JARM module attempts to actively fingerprint an SSL/TLS server via a series of TLS Client Hello packets to extract specific responses that can be used to quickly identify default applications or malware. As the scans are ongoing, here are some preliminary numbers. Log in to app.binaryedge.io and query this data now:
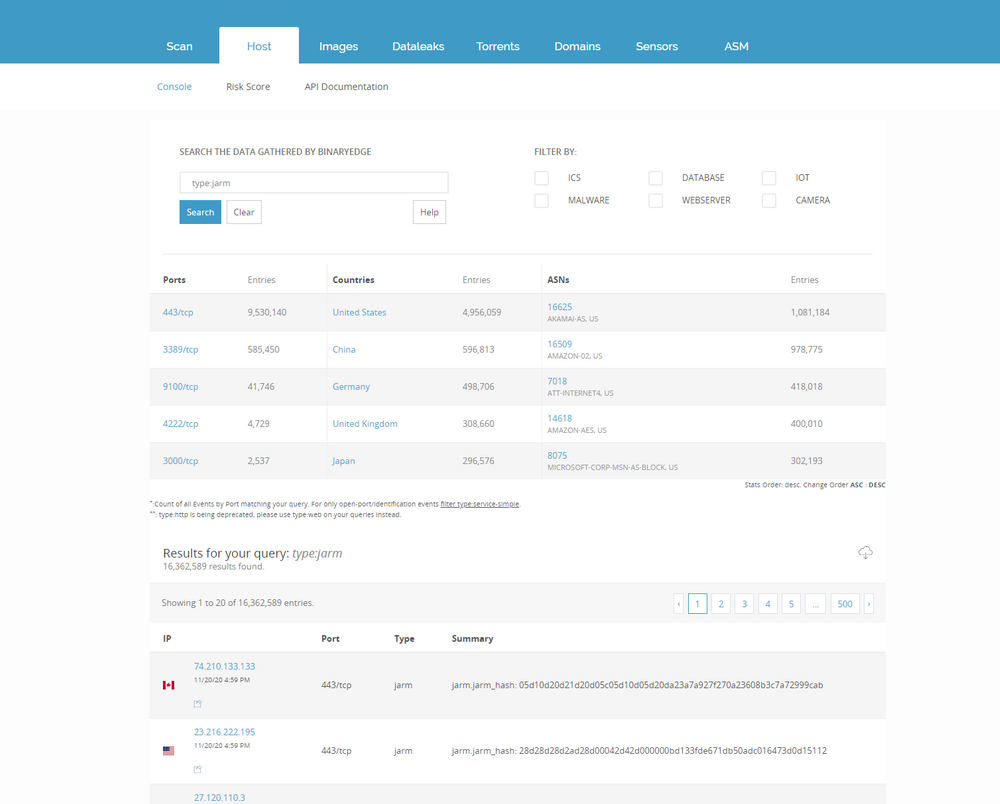
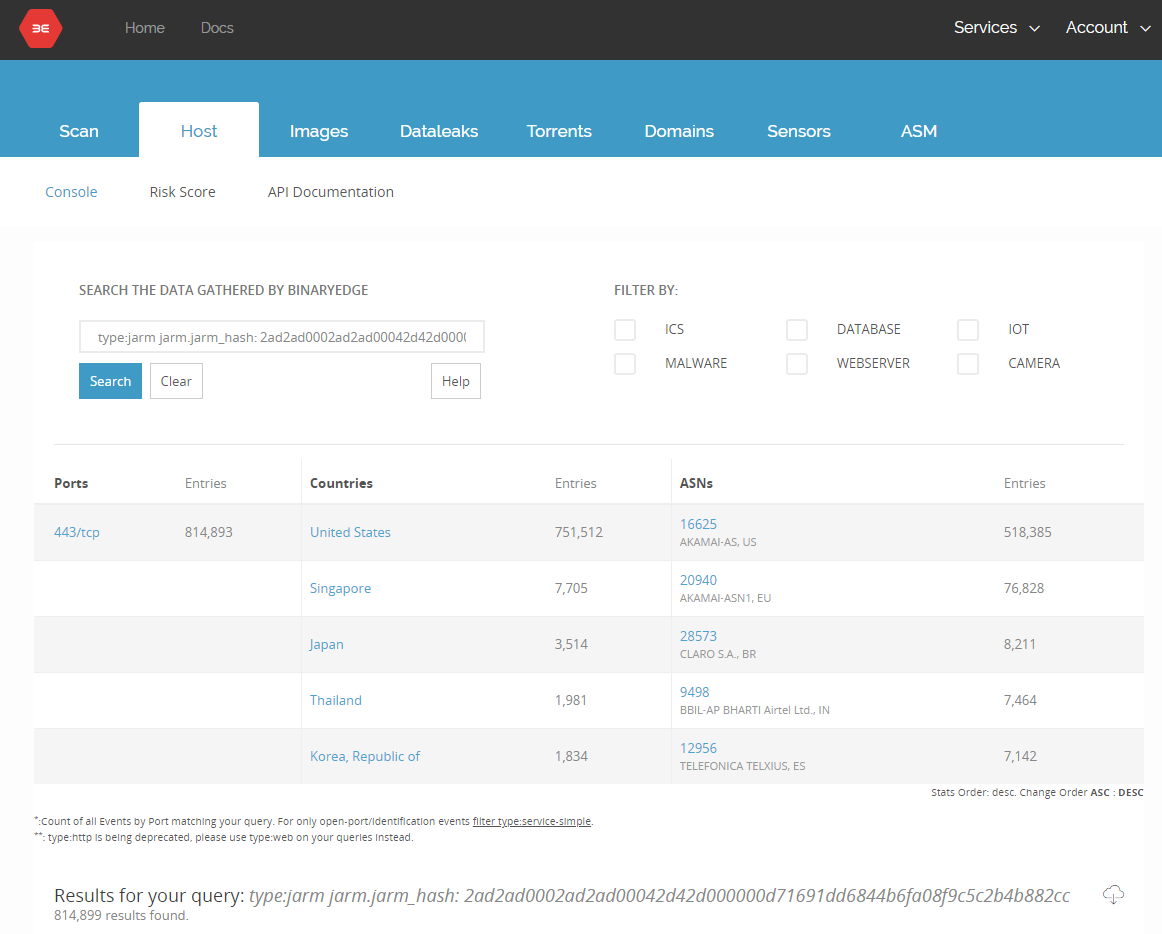
You can also look for specific hashes by using jarm.jarm_hash:"HASH"
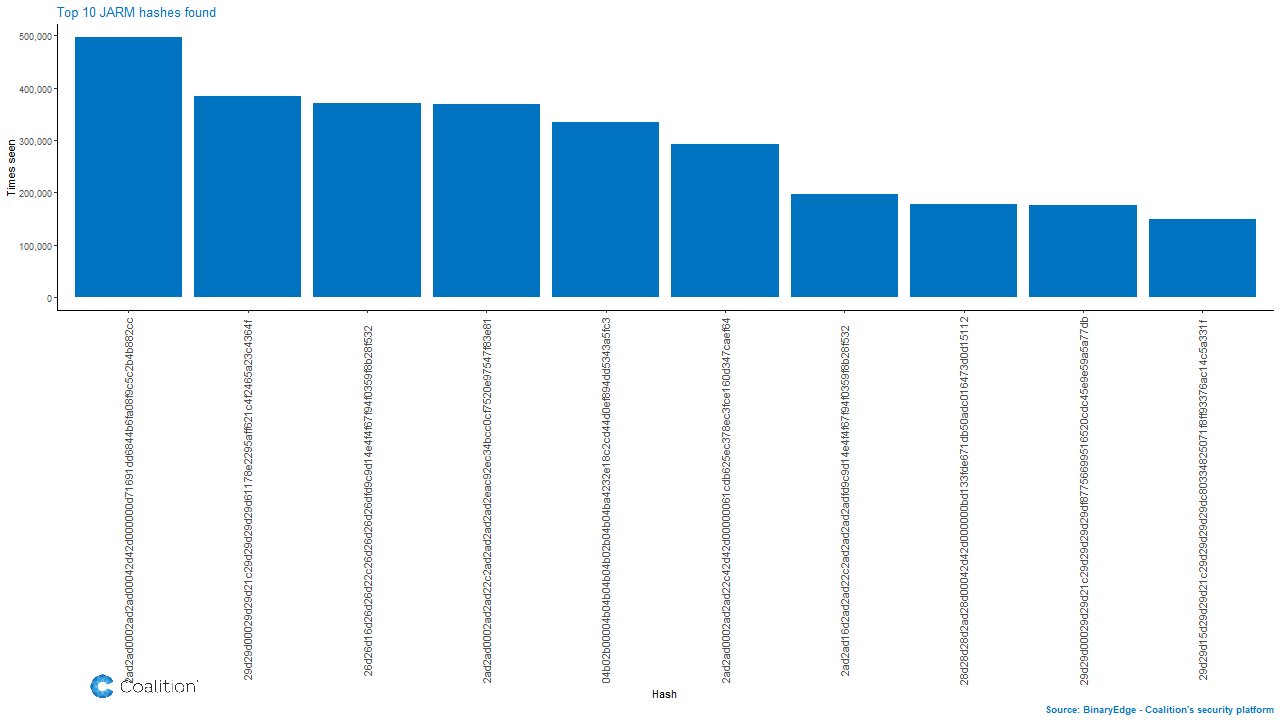
Because the scans are still running, this data may change over time, but as it stands, the most found hash is the AkamaiGHost.
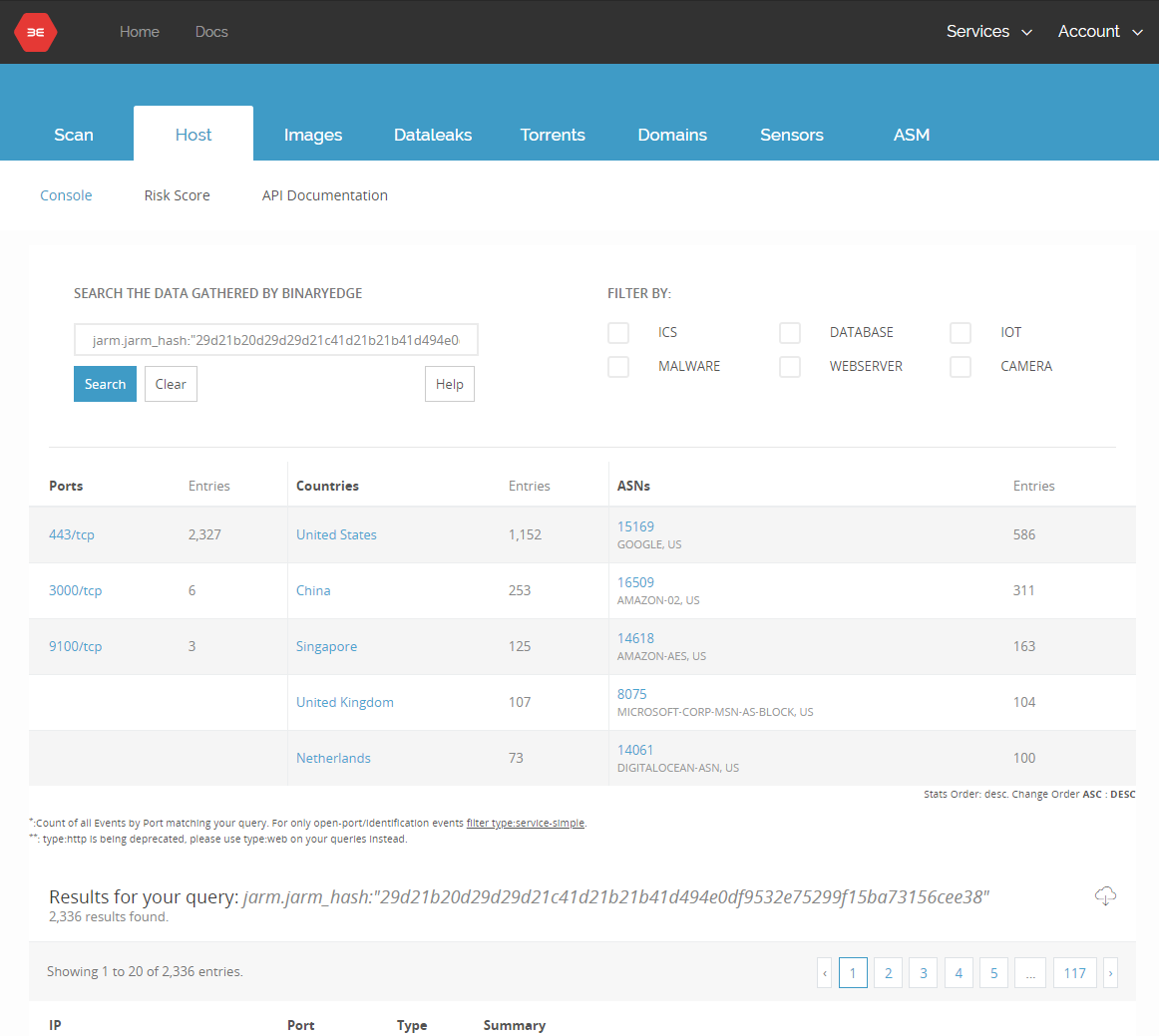
In terms of interesting hashes, the Salesforce team published an initial malware and offensive tool signature list:
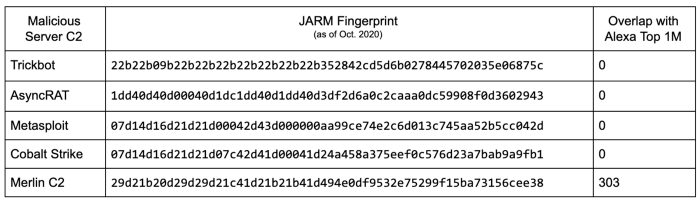
We've already started to detect some of these signatures and more are being added right now as you read this post.
If one of your IP addresses is detected with one of these malicious hashes, you should consider quarantining the machine. If you're a policyholder, Coalition is prepared to help you with the assistance of our Security and Incident Response Team.
Cobalt Strike
Merlin C2
If you're an ASM customer or a policyholder, you will be automatically notified if any of your assets are found with these dangerous signatures. Our team looks forward to adding more signatures of known malware soon.
Server Message Block (SMB)
Scott Walsh published a blog post recently about his efforts to improve our ability to detect and communicate with exposed Server Message Block services.
To quote Scott's post:
SMB is a networking protocol that originated at IBM, but was adopted and implemented by Microsoft circa 1990. Let's just say that 1990 was a more trusting time, and the ability to easily share information greatly outweighed the need to secure it — the concept of the internet as we know it today was not being considered in an adversarial lens.
This is now available to all customers as a module for custom scans and from the portal by using:
type:smb
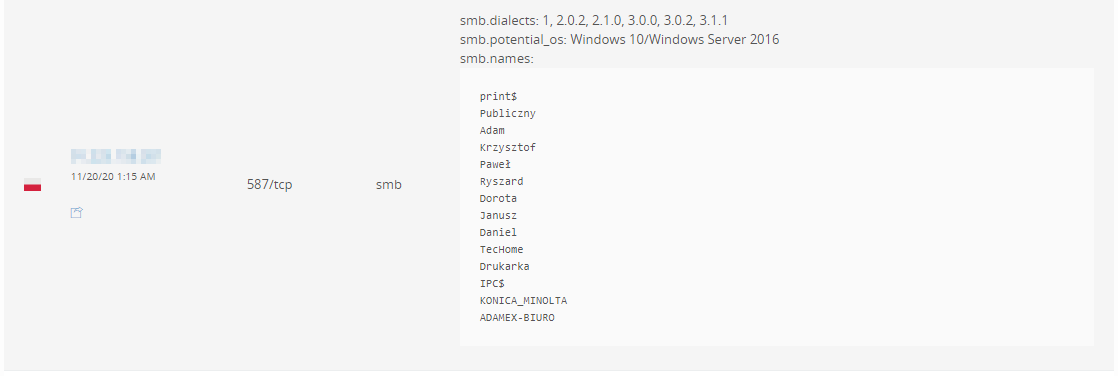
This new module lists exposed share names, OS version, and dialects available for SMB. As usual, if an SMB share is found open, all policyholders that use our Attack Surface Monitoring will be quickly notified.
Make cybersecurity a priority
Coalition is constantly adding more features to our security platform, BinaryEdge. This benefits our policyholders because they get scanned regularly and are notified of any new vulnerabilities or issues found within their assets at no additional charge.
If you want to dig deeper into your security data, please reach out to us and get set up with an Attack Surface Monitoring account (free for policyholders). Or, if you'd like to check out ASM, we'd be happy to give you a test enterprise account.








