Security Alert: MOVEit Zero-day Exploited for Data Theft

The situation regarding MOVEit continues to evolve, and remediation guidance is changing rapidly. We anticipate that additional patches are likely, especially as Cl0p continues to publish a list of victims and exfiltrate data. Ensure you check Progress Software's website for the latest information on patching and remediation.
Coalition Security Labs, our security research and innovation center, has been monitoring the events surrounding the latest zero-day critical vulnerability in MOVEit Transfer. Following Progress Software's public disclosure of the vulnerability on May 31, 2023, we began gathering information to notify impacted policyholders and update our honeypots.
Impacts to file transfers at scale
MOVEit is a managed file transfer (MFT) solution that securely transfers files across organizations using different protocols (SFTP, FTPS, SCP, HTTPS) and is available both on-premise and as a cloud-based software-as-a-service (SaaS) solution. The vulnerability impacts cloud-based and on-premise versions of MOVEit.
The vulnerability (CVE-2023-34362) is being exploited by threat actors who are mass-downloading data in transit from organizations using the MFT solution. Developers warned organizations to "block external traffic to ports 80 and 443 on the MOVEit Transfer server." The developers also warn to check the 'c:\MOVEit Transfer\wwwroot\' folder for unexpected files.
On June 5, 2023, Microsoft published research attributing the ongoing exploitation to the threat actor Lace Tempest. According to Microsoft, this threat actor is a ransomware affiliate known for ransomware operations with ties to the Cl0p extortion site. Microsoft noted that the threat actor has a recorded history of using similar vulnerabilities to gain unauthorized access, steal data, and extort victims.
Mandiant also found potential links to the FIN11 financially-motivated threat group, also known for data theft extortion attempts through the Cl0p ransomware leak site.
The National Cyber Security Centre (NCSC) issued a statement that they are assessing the impact of the MOVEit vulnerability and urged impacted organizations to take action to mitigate their exposure. Similar concerns were echoed by the Government of Nova Scotia, which was among the companies suffering downstream impacts after payroll provider, Zellis, was impacted by the MOVEit vulnerability.
How Coalition is responding
Whenever a new zero-day vulnerability is published, our first step is to use our existing honeypot and scanning data to identify policyholders utilizing the vulnerable technology. Notifications to our affected policyholders were sent on June 1, 2023, advising them to implement the remediation steps released in the announcement. Policyholders received this alert via email and our risk management platform, Coalition Control.
This vulnerability, CVE-2023-34362, is a SQL injection exploited via the HTTP or HTTPS interface. Utilizing indicators of compromise outlined in the public disclosure, we can retroactively see reconnaissance performed in the wild.
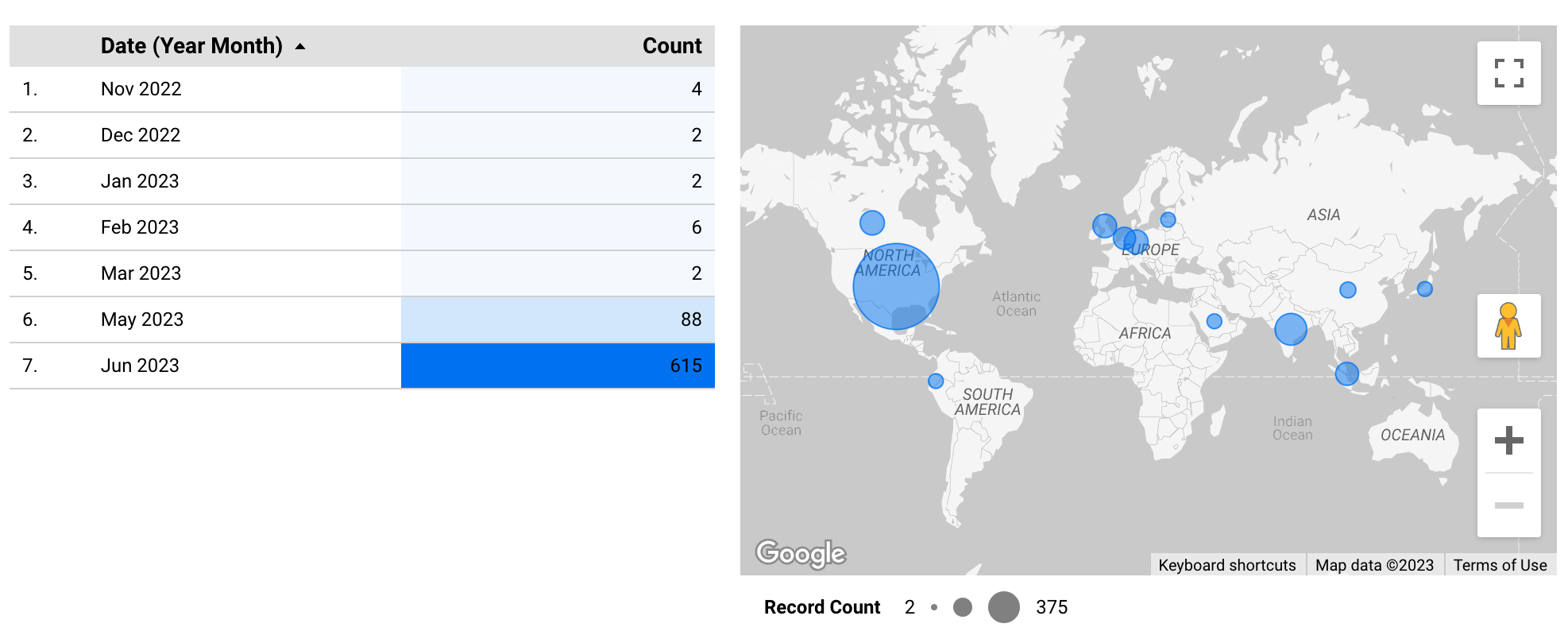
The first key indicator of compromise (IoC) is the /human.aspx path. This is typically the path to the login page for MOVEit systems. Looking at our honeypot data, we saw HTTP requests to this path as far back as November 2022 and periodically since then, with minimal traffic. Then, on May 15, 2023, we saw a large spike in traffic to this path. This data seems to indicate that threat actors are conducting reconnaissance to assemble a list of targets to exploit.
Coalition Honeypots— Recon for MOVEit '/human.aspx'
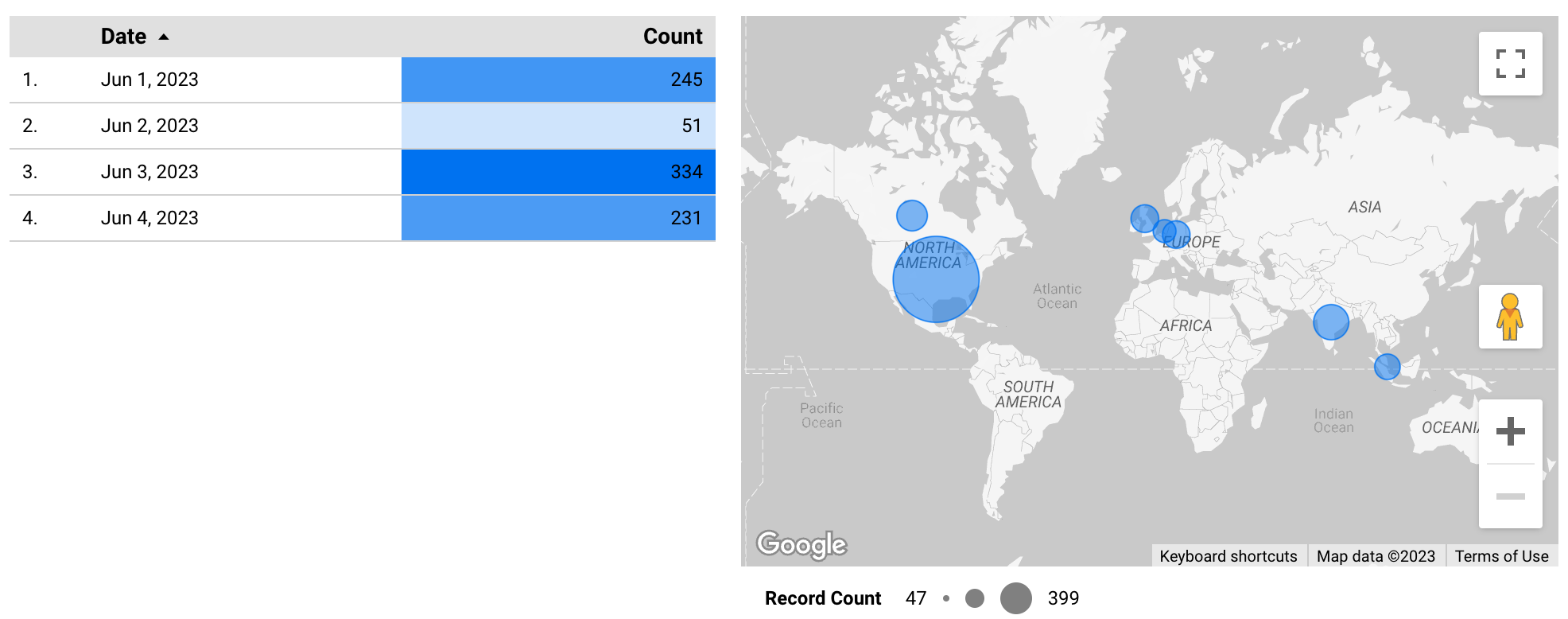
The second key IoC is the peculiar /human2.aspx path. This indicates an attempt to exploit the vulnerability. Looking at our honeypot data, we began seeing HTTP requests to this path on June 1, 2023, just one day after the public disclosure. This traffic spanned a wide range of IPs, indicating attempted mass exploitation. Subsequent samples of the content of human2.aspx revealed that without a specially crafted request, including a password set during the initial compromise, that access would be denied.
Coalition Honeypots— Recon for MOVEit '/human2.aspx'
Going forward
Coalition Security Labs will use the information around this vulnerability and our honeypot data to improve our ability to identify potential threats before they emerge.
We strongly recommend all organizations impacted by this vulnerability take the necessary remediation steps. Progress Software will continue to detail the latest remediation instructions, and it is likely that additional patches will be released.
Impacted parties can learn about specific vulnerabilities impacting their digital infrastructure through Coalition Control™. Included in Control is Vendor and Third-Party Monitoring, a feature that allows organizations to keep a careful eye on the companies and suppliers they partner with, helping to mitigate the risk of supply chain disruptions. These insights can help security decision-makers understand the ramifications of third-party risk for their organizations and respond accordingly.








