It's a Trap — Honeypots Help Defenders Gather Threat Intel

This post was authored by Shelley Ma, MS, EnCE, Coalition Incident Response Lead, with additional contributions by Simon Bell, Ph.D., Coalition Cybersecurity Researcher.
Before becoming a cybersecurity tool, honeypots were an espionage technique in which spies used physical relationships for blackmail and coercion. In today's digital economy, honeypots still serve as a decoy; they are digital assets that can be made to look like legitimate devices, such as servers, payment gateways, or networks, but instead acts as a decoy to trick threat actors. The organization that deployed the honeypot uses it to gather information about the attackers, such as their tactics, techniques, and procedures (TTPs).
The honeypot must resemble a legitimate target. This is critical because the honeypot must be convincing enough for a threat actor to believe they have access to your network. If the threat actor believes the honeypot is legitimate, they will ideally spend time carrying out their attack within this controlled environment, allowing response personnel to gather intelligence about the threat actor while detecting cyber attacks.
Honeypot benefits and risks
A well-designed honeypot can serve as an excellent entrapment strategy that encourages threat actors to waste their time within the decoy environment — and not in your network. Let's review some of the benefits and risks associated with honeypots.
Benefits
The intelligence gathered from honeypots can be very useful in helping companies develop or enhance their security strategy and gather information continuously.
Honeypots can shed light on blind spots in your architecture and provide a real-time look at attack methodologies.
Honeypots can highlight internal security risks due to error or misuse of resources. The 2022 Verizon DBIR found that error was responsible for 13% of breaches.
Honeypots allow the security operations center (SOC) to fight alert fatigue. By comparing honeypot and perimeter attack patterns, you can distinguish internet noise from attacks targeting your organization. This internet noise can then be tagged, allowing your analysts to focus on what’s important.
Risks
Because honeypots must be well-designed to convince threat actors, they can put a bullseye on your organization.
Misconfigured honeypots can enable threat actors to move laterally within your network and potentially elevate their privileges to access sensitive business data.
Honeypots should only be developed and deployed by experienced security practitioners.
While you don't need a dedicated SOC to run a honeypot program, they will require maintenance and response to any threat detections. Security analysts can review honeypot traffic to understand what services are being targeted and which vulnerabilities are being exploited. Those in the digital forensic and investigation (DFIR) field understand the importance of reviewing logs, e.g. from Security Information and Event Management (SIEM), to understand how any attackers got into the system. Well, the same is true for honeypots. Logs, generated by honeypots, can be analyzed by security personnel to understand the attacker’s TTPs – but luckily no system has been breached.
Types of honeypots
Honeypots can emulate a range of services, offering varying levels of functionality and complexity. There are typically four main types of honeypots, each with different levels of interaction.
Low-interaction honeypot
Typically designed to emulate one specific service (such as a database), low-interaction honeypots will respond to a limited set of actions. While these honeypots are quick to set up and easy to deploy, they are usually easy to identify, and attackers may show little interest in them.
Medium-interaction honeypot
Often emulating one or more services (such as a web server, database, etc.), medium-interaction honeypots can respond to more advanced commands. As a result, these honeypots may require more specialized knowledge to set up but may be more convincing to threat actors due to the increased range of responses.
High-interaction honeypot
Designed to look as convincing as possible, high-level interaction honeypots strike a balance between being convincing, while still being relatively safe to deploy. They offer a range of emulated services and responses, and thus attackers are likely to be convinced that high-interaction honeypots are the real deal. Convinced they have found a legitimate target, a threat actor is more likely to flex their full range of attacks on a high-interaction honeypot, revealing more of their TTPs to security researchers.
Pure honeypots
These are fully-fledged operating systems configured with known vulnerabilities and weaknesses. These honeypots require expert knowledge and supervision to design, deploy, and monitor. Since these honeypots are actual systems, they are the most convincing to attackers. However, due to their complex nature, pure interaction honeypots carry the most risk and require considerable time and resources to run.
Before setting the trap: implement the basics
While honeypots can be an important part of a cybersecurity strategy, it's always best to start with the basics.
There are many low-cost and easily deployed defensive measures that companies should focus on to create a defense-in-depth security strategy. We recommend all organizations implement multi-factor authentication (MFA) as well as a strong password management policy. Endpoint detection and response (EDR) tools work to detect and respond to the presence of threats on your network while maintaining (and testing!) offline backups of critical business data. This is essential should you ever become the victim of a ransomware attack. Without a strong foundation, honeypots will likely add no value to your security strategy.
Coalition and honeypots
Coalition seeks to understand not only what new vulnerabilities are announced but also how threat actors use them. This is an important piece of the puzzle we use to stay one step ahead of threat actors.
To that end, we create honeypots that appear as vulnerable machines to both researchers scanning the internet and potential threat actors scanning the machines. This allows Coalition to see what trending vulnerabilities attackers are exploiting, and if there are newly discovered vulnerabilities that have yet to be announced.
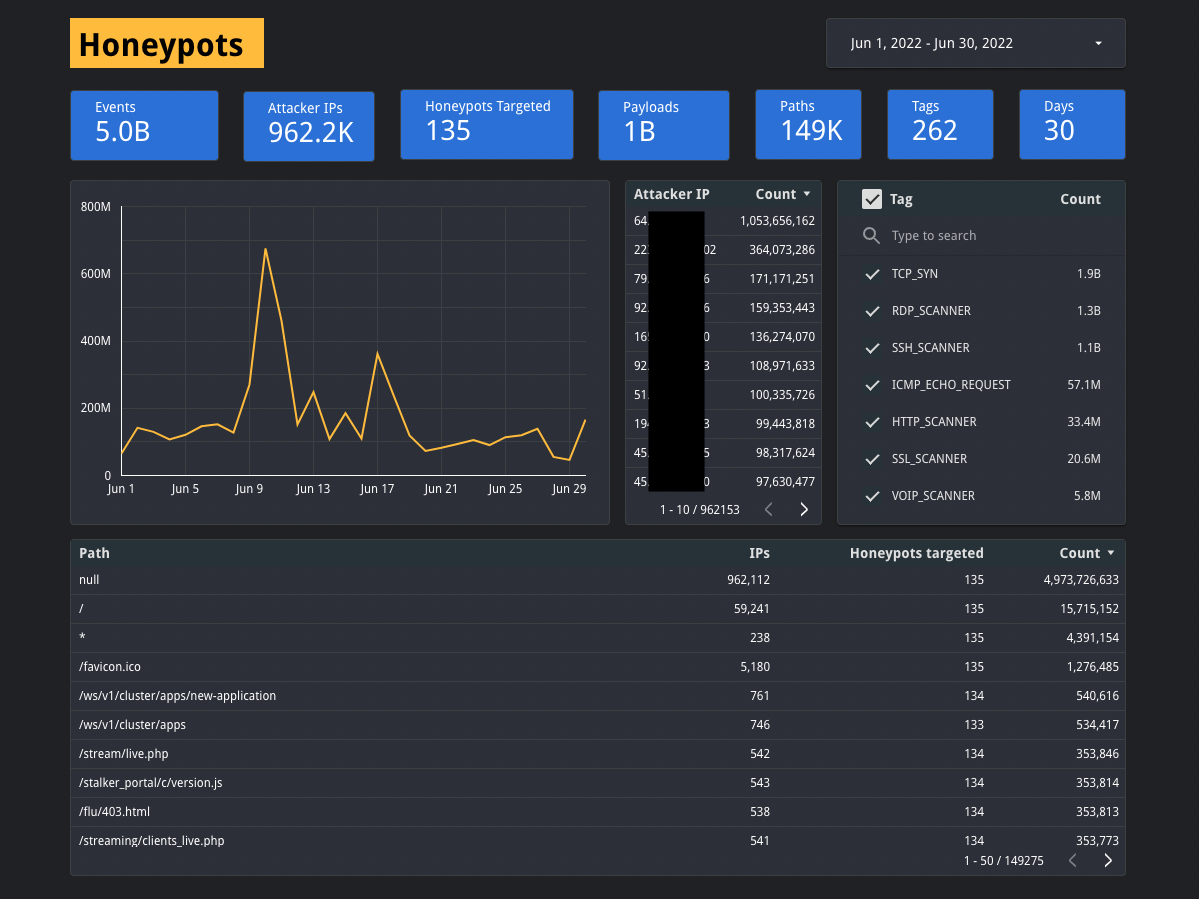
Screenshot of our honeypots dashboard showing 5 billion events during June 2022.
We have an entire team focused on building fake, vulnerable honeypots that emulate business networks and pose as such on the internet. The information garnered from Coalition’s honeypot operations helps our cybersecurity team inform the future protection of our policyholders.
When a new vulnerability (such as Log4j) is discovered, we typically see attackers targeting it on our honeypots. These attacks give us crucial intelligence about how popular and widespread the vulnerability is being exploited in the wild. Our honeypots are deployed across the globe, allowing us to detect geographic patterns and monitor trends across service providers.
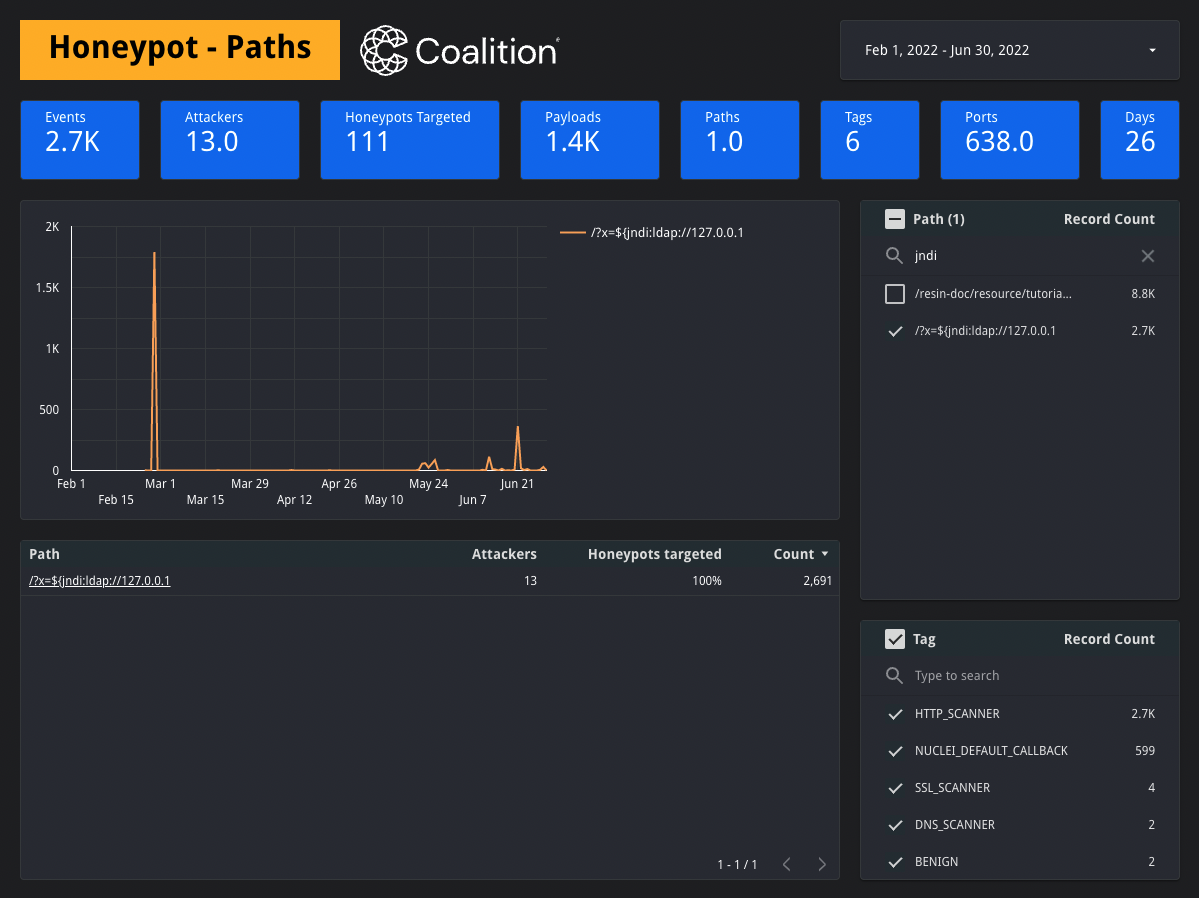
Screenshot of our honeypots dashboard showing a Log4j payload: /?x=${jndi:ldap://127.0.0.1
Alongside our honeypots, we also deploy sinkholes. These devices capture all network traffic sent to them, producing valuable data and insights into global network activity. Even if a new vulnerability comes out that we don’t have a honeypot for, we still capture the important payload traffic on our sinkholes. We also detect network activity with our sinkholes that honeypots would miss.
By combining our honeypot and sinkhole intelligence with analysis about a vulnerability, we can understand the impact that a vulnerability may have on our policyholders. We can then rapidly inform our policyholders on how best to mitigate and stay safe from cyber attacks.
If you want to see the vulnerabilities that might exist on your network, log into Coalition Control now.







