The Evolution of Ransomware — a cyber claims perspective
Like any virus, ransomware will always find a way to evolve. I've seen this evolution firsthand over the last decade serving as in-house counsel, and especially on the Claims team here at Coalition.
For brokers, it’s more important than ever to advise your clients on the risks that can lead to ransomware. It also creates an opportunity to become a more trusted risk advisor. To better understand how ransomware evolved to where it is today, let’s go back to the beginning with some of the first cyber claims.
The dawn of ransomware
At the core, ransomware is just a program that encrypts data. There's a range in the sophistication of ransomware variants that have cropped up over the years.
With the first cyber claims I handled in 2013, the organizations targeted by threat actors had personally identifiable information (PII) or trade secrets, and the victim’s data would subsequently be sold on the dark web. The monetary demands from bad actors were also much lower because acquiring cryptocurrency was difficult.
Here's an example from those early days. One insured I worked with found her laptop encrypted with the CryptoLocker virus and a rudimentary note requesting $500 in Bitcoin. The insured had business receipts valuing more than the ransom on her laptop, so she elected to pay.
The insured used a physical crypto ATM to receive the private key for a crypto wallet and remitted the ransom payment to the threat actor in person. It was up to the victim to deal with these amateur extortionists.
The emergence of sophisticated attacks
As technology evolved, so did the sophistication of threat actors. Cyber criminal groups got organized. We saw them spend more time on reconnaissance, targeting larger organizations with more to lose.
Threat actors started to use hack toolkits to "prep" the system for the attack. They made efforts to cover their tracks on the way out. They no longer required in-person meetings with victims to pay the ransom because they accessed a quicker way to get paid through digital cryptocurrency.
I remember having this epiphany moment when I started seeing many more claims. It was in 2017, right around the time of WannaCry — the ransomware cryptoworm that targeted Microsoft Windows users — that we saw cyber incidents happening on a widespread corporate scale.
It was no longer just individual laptops but entire networks. Threat actors were targeting banks, governments, and hospitals because they were more lucrative. There was a stronger likelihood that the extortion would be successful if there was a potential to bring things to a halt.
Back then, law enforcement groups said, ‘don't pay, don't pay.’ The hardline was you don't engage with criminals. And as this decade has gone by, it has become clear that ransomware isn’t going away, and it is debilitating to businesses.
Those of us working in the insurance industry saw law enforcement collectively change its stance as if to say, 'Whether you pay or not, we are agnostic… you have a business to run…' and these were the ones that were actually saving lives.
To me, that was the watershed moment when law enforcement changed its position.
Fast forward to ransomware today
Now we know that cyber criminals are industry agnostic; they're looking for low-hanging fruit to make money. Since 2019, many groups have changed their tactics to include data exfiltration along with encryption to increase their chances of getting paid.
We’ve seen an ecosystem pop up with interconnectivity and collaboration among threat groups. These are professional operations running 24/7. They are businesses with online tech support, infrastructure, and coordinated efforts like a ransomware assembly line.
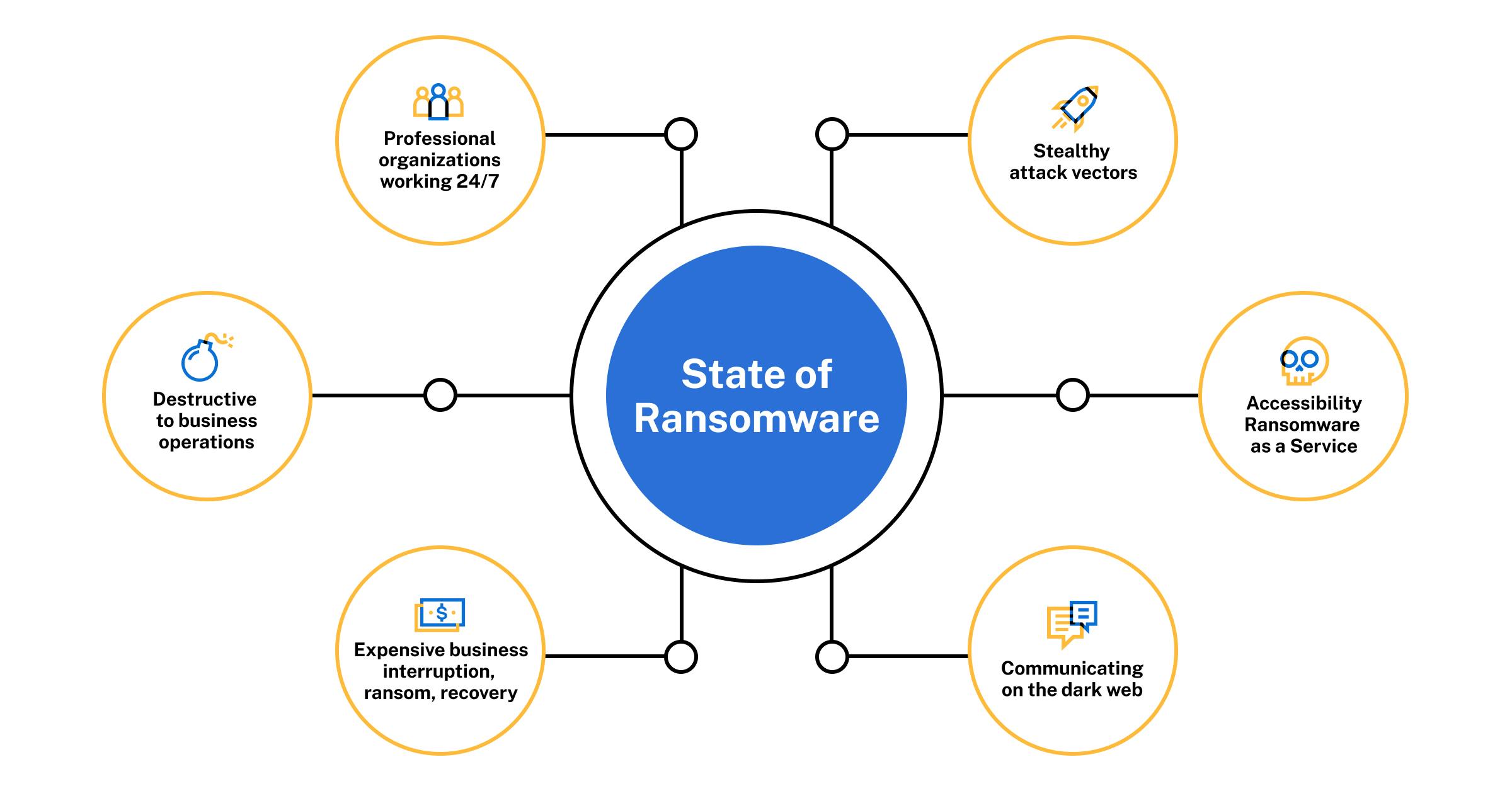
It’s ransomware-as-a-service where all aspects of an attack get assigned or outsourced. They are stealthy in their attack vectors. Communication for hackers is easier than ever on the dark web. They found new ways to be more destructive and expensive, with additional costs racking up from business interruption and recovery — and I've been there helping impacted organizations as a "breach coach."
I joined Coalition in 2020 when ransomware was exploding. The rise in ransomware is directly correlated to people pivoting to remote work. In a brick-and-mortar office, you can turn to your fellow employee to confirm if an email looks suspicious. Threat actors knew this, and they jumped on the opportunity.
Coalition is here to help
It's doubtful that threat actors will abandon a thriving criminal business model. Our most recent Claims Report shows that phishing accounted for over half of reported claims. A phishing email can often include a malware attachment, and that malware can lead to ransomware.
There's no total remedy to prevent a cyber incident. It breaks my heart to know there will always be bad actors out there wreaking havoc. But that’s where Active Insurance goes such a long way. At Coalition, we use our technology to constantly scan our book of business to see how we can be proactive on the front end to alert our policyholders of the biggest digital risks.
Coalition Control offers free attack surface monitoring for any organization; you don't need to be a cyber insurance policyholder to get some of the benefits of our cyber risk management platform. And you can also help your client understand the risks of cyber attacks by creating their specific risk profile with Coalition's Risk Assessment.
I came to Coalition to grow my career in cyber. My colleagues and I are here to help. We can work together to create a better future over the next decade.








