Free third-party risk management in Coalition Control: monitor your supply chain
Attack surface monitoring is just one part of a holistic approach to cybersecurity. Keeping your attack surface as small as possible is a solid goal for any security or cyber risk management leader. However, as organizations’ digital footprints are constantly evolving, growing and shrinking over time, it can be challenging to maintain visibility — let alone control — over your organization's attack surface in a comprehensive and ongoing manner.
Coalition Control offers free attack surface monitoring for any organization, but it doesn’t stop there. Understanding the needs of the modern business, we’ve included third-party risk management to help organizations manage their cyber sprawl. “What’s third-party risk management,” you ask? Sign up for a free Coalition Control account here, and then we’ll continue digging into this hot topic. Done? Cool, let’s go!
What is third-party risk management?
Cloud vendors, IT service providers, external software management firms are examples of third parties — nearly all organizations assume some level of third-party risk as part of operating in a digital world. As a result, third-party risk management (TPRM) is a critical consideration in business right now, as high-impact supply chain attacks have highlighted the need for visibility and control over systemic digital connections. Essentially, TPRM is a concept that enables organizations to see the potential risk impact third parties, such as vendors, suppliers, and partners, pose to their operations.
To get a deeper understanding of TPRM, let’s think about two examples.
The first example is simple. Imagine you use a software-as-a-service (SaaS) solution for your accounting system. There are many of these solutions available, and many of those are household names. If that vendor were breached and your login credentials were compromised, you’d want to know right away. Third-party monitoring helps to track these risks in real-time, and in this scenario, you’d want to consider adding your accounting SaaS vendor to your Coalition Control Watchlist.
The second example is a bit more complicated. Let’s say you have a customer that has access to your inventory through a real-time feed that powers their eCommerce content management system. If this inventory feed lives on a database and that database is not configured properly, a threat actor could potentially gain access to your own organization’s sensitive data due to a compromise of your customer’s infrastructure.
These two examples illustrate how easily the risk of operating in a digital economy can translate into an adverse cybersecurity event. Keeping an eye on your third party risk can help you get ahead of threats by finding and fixing problems before the bad guys can exploit them.
Free third-party risk management
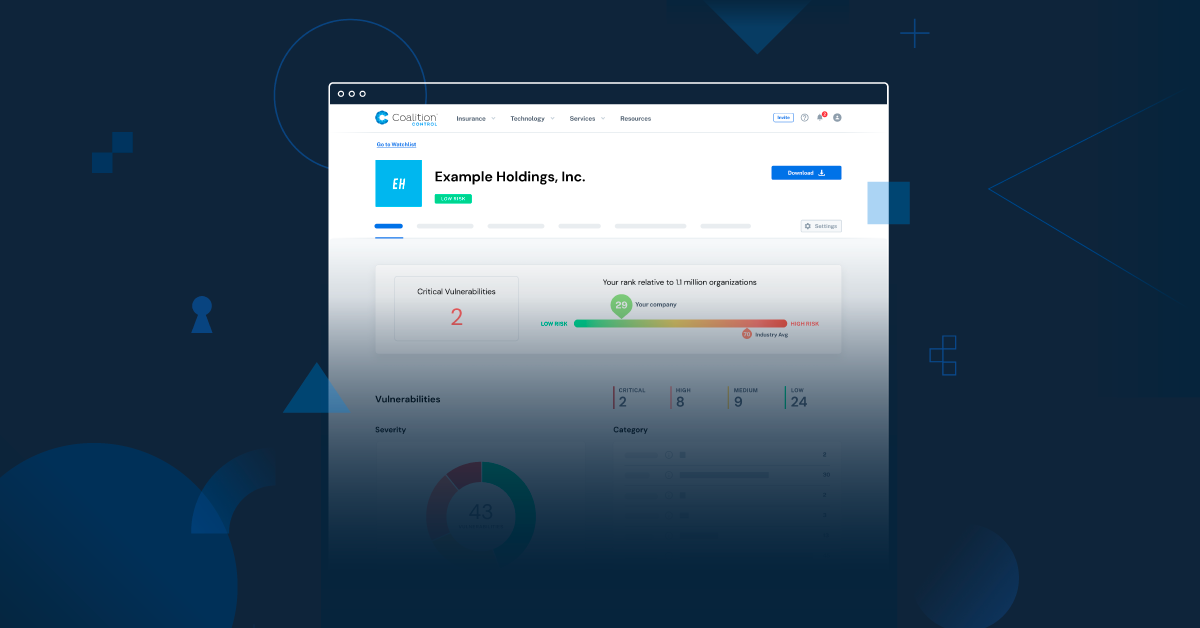
Coalition Control offers free third-party risk management via what we call a ‘Watchlist.’ Adding your vendors, suppliers, and partners will alert your organization when new critical vulnerabilities are discovered on the internet-facing assets of those third parties. This is a huge value-add for all Coalition policyholders (and free users, too) that enables a holistic view of much of their risk footprint.
To watchlist a company or vendor, click ‘Go to Watchlist’ on your organization’s summary page, then click ‘Add Company.’
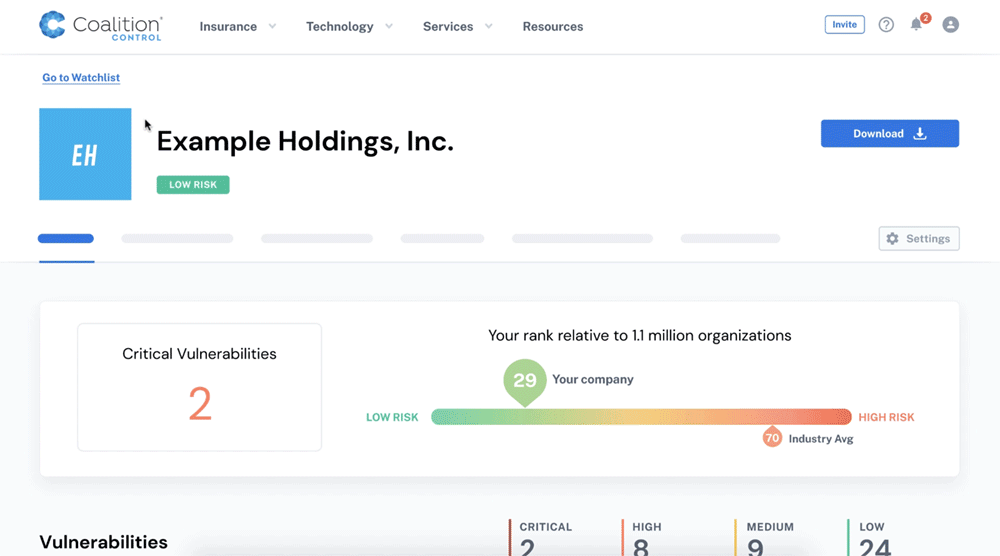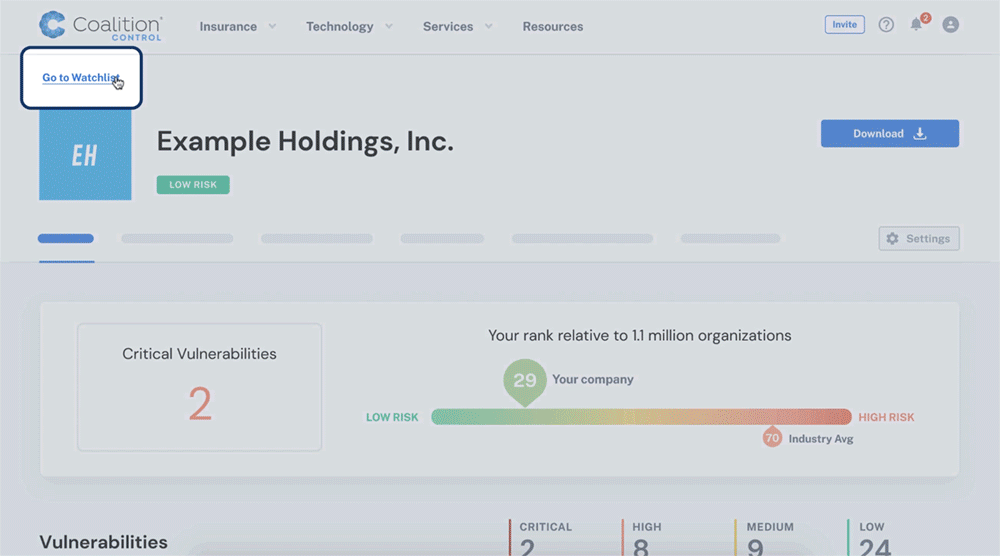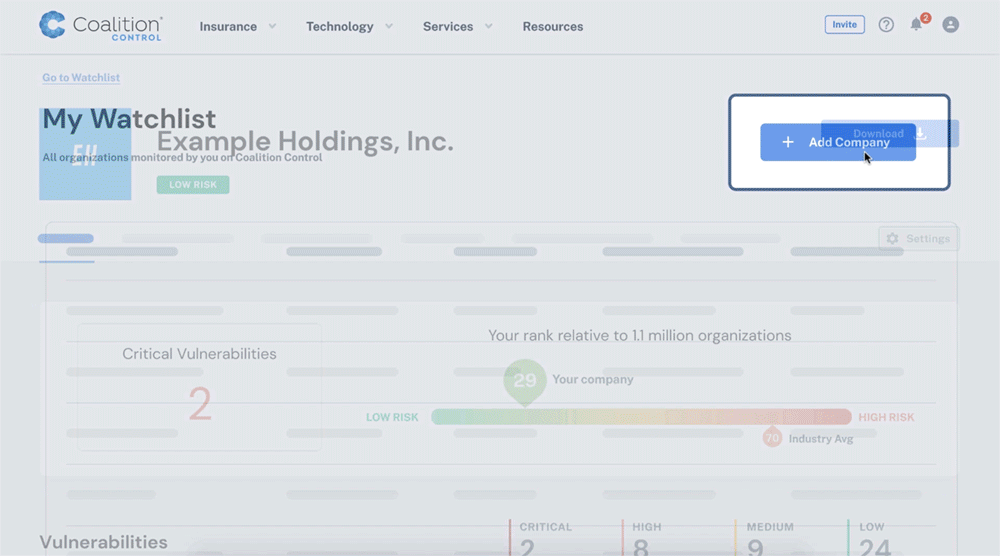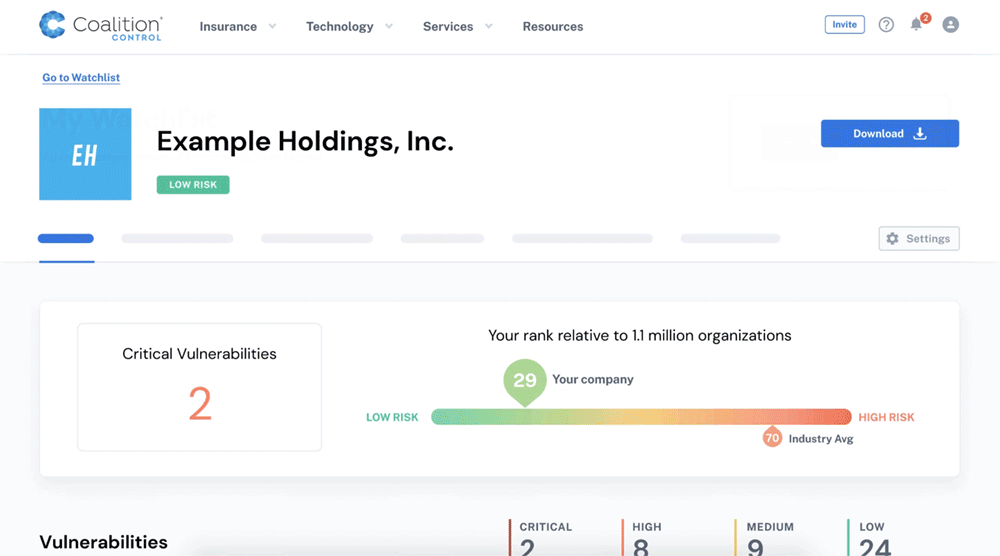
Fill out the fields as prompted for the organization you wish to monitor. For example, you can simply enter a company name (to label the organization in your Watchlist) and a domain. Do not include the ‘www’ at the beginning of the domain name.
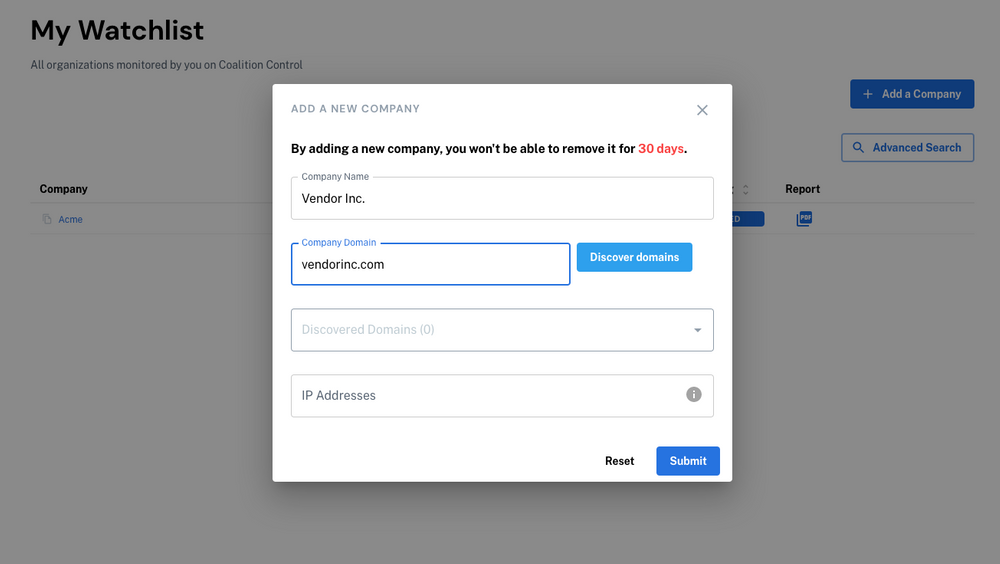
If you do not have a complete list of your third-party vendor’s domains, you can use our domain discovery service by clicking ‘Discover Domains’ to add the domains we can find. Then, click ‘Submit’ to add the third-party’s domain to your Watchlist and receive alerts whenever critical vulnerabilities are discovered on their public infrastructure. As with your organization's Control dashboard, you can also identify less critical vulnerabilities and determine whether those items are a risk to your operations.
The Coalition difference
We know there are many different ways to manage, mitigate, and transfer risk. You might already be bombarded with vendors and solutions providers seeking your commitment to their products, and that’s not necessarily a bad thing.
In reality, Coalition wants you to mitigate your risk in any way possible, and we want to help you lower your risk no matter what. That’s why we make Coalition Control available for free to any organization, regardless of what technology they use or how they ultimately manage their risk posture.
Naturally, should an organization choose to transfer their risk through comprehensive cyber insurance, we offer the industry’s leading coverage — at a time when many other carriers are reducing theirs. Sign up for free, and take control of your risk today







