Kaseya Ransomware attack: Respond now to protect your organization

Kaseya, a remote management solution typically used by multiple managed service providers (MSP) in the United States to help manage their clients' systems, was the victim of a ransomware attack executed on July 1, 2021. The threat actors that compromised Kaseya are now using the Kaseya software to access customer networks and deploy ransomware.
I use Kaseya or my MSP uses Kaseya. What should I do ?
If your organization uses Kaseya Virtual System Administrator (VSA) server, firewall it off from the internet and restrict access immediately. You can do this by configuring your firewall or internal network to isolate the server from the rest of the network or shutting down the VSA server.
You will want to make sure your backups/backup server is isolated from the rest of your network, including the network where your Kaseya server is located. Threat actors have already been observed targeting and deleting backups, such as Veeam, Sophos, and other backup technologies.
Kaseya has put out a statement:
We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shut down your VSA server until you receive further notice from us. It's critical that you do this immediately, because one of the first things the attacker does is shut off administrative access to the VSA.
How to get in contact with Coalition
The Coalition Incident Response team (CIR) is ready and prepared to help you during this event and answer any questions you may have. Even if you have not been affected by the ransomware, Coalition can help with preventative measures; please reach out – we’re here to help.
All policyholders with an issue, please call 24x7 toll-free at +1 833 866 1337 or email security@coalitioninc.com . The sooner, the better.
How do I know If I’m affected?
At this time, Coalition is unable to assess who may be affected; however, there are steps you can take to evaluate the risk to your organization. For example, if you start to notice abnormal behavior across your servers or workstations, including, but not limited to, changes in file names and desktop background images, you might have already been affected.
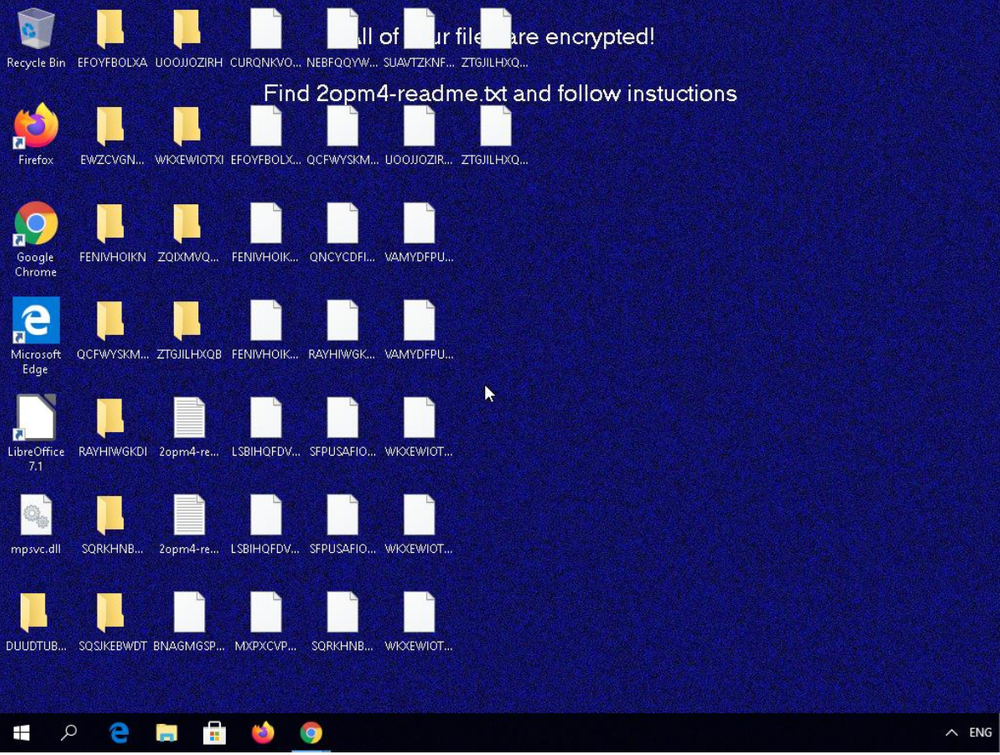
Reach out to your MSP if you are unsure if they use Kaseya and feel free to include Coalition in this communication. If you are a system administrator the following technical information can be of use to identify the vulnerable software:
Any connections on your firewall logs to/from kaseya.com / kaseya.net
Presence of a file called “agent.exe” in c:\kworking\agent.exe
File Hash (d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e)
Presence of the file mpsvc.dll
File Hash (8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd)
Any connections on your firewall logs to/from kaseya.com / kaseya.net
Presence of a file called “agent.exe” in c:\kworking\agent.exe
File
Hash(d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e)
Presence of the file mpsvc.dll
File Hash (8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd)








