September Risk Roundup: Planned cyber counterstrike leaves businesses without ransomware remediation

In mid-July, the notorious hacker group REvil briefly went offline. We now know REvil's hiatus caused them to narrowly avoid an FBI counterstrike for a slew of ransomware attacks. These attacks impacted small towns in Maryland, schools in New Zealand, the world's largest meat supplier, and remote management solution provider Kaseya. While their hiatus was not caused by government intervention, the FBI still held onto the decryption keys, which could have significantly benefited REvil's victims, including schools and hospitals. As ransomware attacks continue to proliferate, the chance at a counterstrike seems thrilling. Still, it is crucial to balance retaliation for cyber attacks with protecting the businesses that stand to lose the most from these events.
1. FBI held back REvil ransomware decryption key from businesses
Three words: fascinating, inspiring, and frustrating. This story is fascinating because we now know there is causal evidence between REvil’s hibernation directly following the attack and the FBI’s proposed counterstrike against them. It’s inspiring because, hey, a counterstrike — this is honestly refreshing to hear and I hope playing offense is a trend that continues and towards better outcomes in the future. Finally, this is frustrating. As the article notes, business owners were crying and pleading with their IT teams to help them, and this level of suffering and existential dread is exactly what governments are supposed to prevent in their constituencies. I’m not saying that in this case there was much that could’ve been done better or differently, but I do hope we carry this lesson into our next counteroffensive operation: time is the enemy, too. Thankfully, one of the benefits of good public-private partnerships is that private companies are very, very fast. – Will Andre, Senior Manager, Product Marketing (Security)
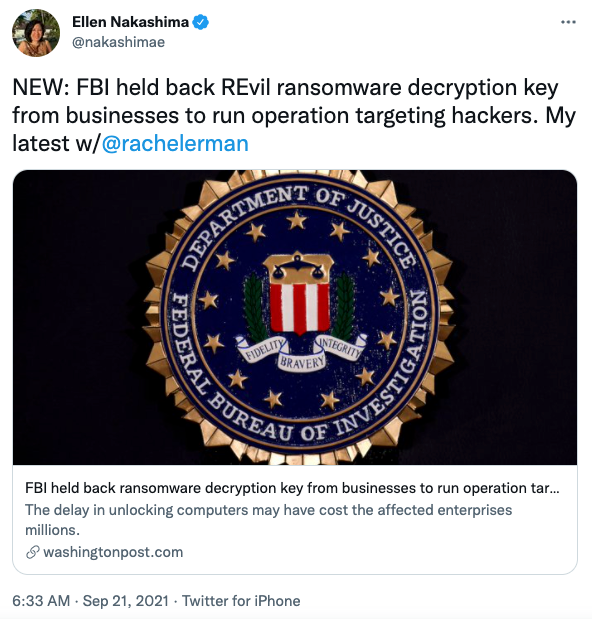
2. BlackMatter ransoms (another) food critical infrastructure
Ransomware gangs don’t care about your data, you care about your data, and that’s why everyone is a target. – Scott Walsh, Senior Engineer
3. Spanish security researcher discloses Apple lock screen bypass
All software has flaws and no company is perfect, but the process for discovering and fixing those flaws is complicated. Apple has been criticized for its handling of bug bounties (basically a way for security researchers to report and get paid for finding bugs); and it appears that Apple’s approach isn’t as ironclad as one would hope. Lockscreen bypass bugs are only possible if an attacker has physical access to your iPhone, but one would hope that Apple could be more responsive to researchers following ethically-sound bug disclosure practices. – Aaron Kraus, Security Engagement Manager
4. No honor between ransomware gangs and their affiliates
Ransomware gangs can’t be trusted — there is no “honor amongst thieves.” Threat actors also frequently tell victims they will reveal how they were compromised after ransom payment. Often, they claim it was phishing when forensics show that the root cause of the compromise was RDP, or VPN exploit. Additionally, this week we saw other ransomware groups break their targeting rules in other high-profile cases. Any time these threat actors can gain an advantage over others, they will. Threat actors are criminals, and their words and actions are untrustworthy. – Tommy Johnson, Cyber Security Engineer
If you enjoyed this post be sure to check our blog weekly; the Risk Roundup runs Friday mornings in addition to more enlightening content we post related to the ever-evolving landscape of digital risk. Follow us on Twitter (@SolveCyberRisk), LinkedIn (Coalition Inc), and Youtube. If you have any suggestions for content that we should be adding to our reading list, let us know!